Good morning. On Friday, I asked LinkedIn for the best cybersecurity caption for this photo of my pup 👇

…and the winner was... 🏆🏆🏆
“In a world of cyber threats, be a good boy”
Those are words we can all live by. But we digress, back to cybersecurity. Today, we’re covering:
Cyber attacks are getting expensive…for businesses and people.
Details on the $25M deep fake heist.
The total cost of Clorox’s ransomware attack.
-Jason
Spotlight
Cyber Attacks are Getting Expensive…

Ransomware is always top of mind when discussing the monetary loss of cyber crimes. And for good reason. Chainalysis, a company that monitors blockchain activity for popular cryptocurrencies, reported that ransomware actors made off with $1.1 billion dollars in ransom payments in 2023. That’s more than five times the amount in 2019! As you can see in the chart below, this hit a record following an unsurprising dip in 2022, when ransomware activity plummeted following Russia’s invasion of Ukraine.

From Chainalyis’s blog post
Financial harm extends far beyond ransomware. The FTC released a report that showed reported fraud topped $10 billion dollars in 2023. That’s a 14% increase from the prior year.
Digging deeper, the highest dollar losses came from investment-related scams. This is where scammers trick people into depositing money into fake investments. The scammers steal the deposit, and the victim is left wondering whether they’ll get their investment back. Spoiler alert. They won’t. In 2023, victims of these scams reported losing more than $4.6 billion dollars. Ouch.
This was followed by imposter scams, where scammers pretend to be someone else and build trust with you. The scammers then get you to send them money. Common impersonations include tech support scams, romance scams, or government impersonator scams. In 2023, victims reported over $2.6 billion dollars in losses. Very ouch.
The FTC put together a great infographic with the combined information.
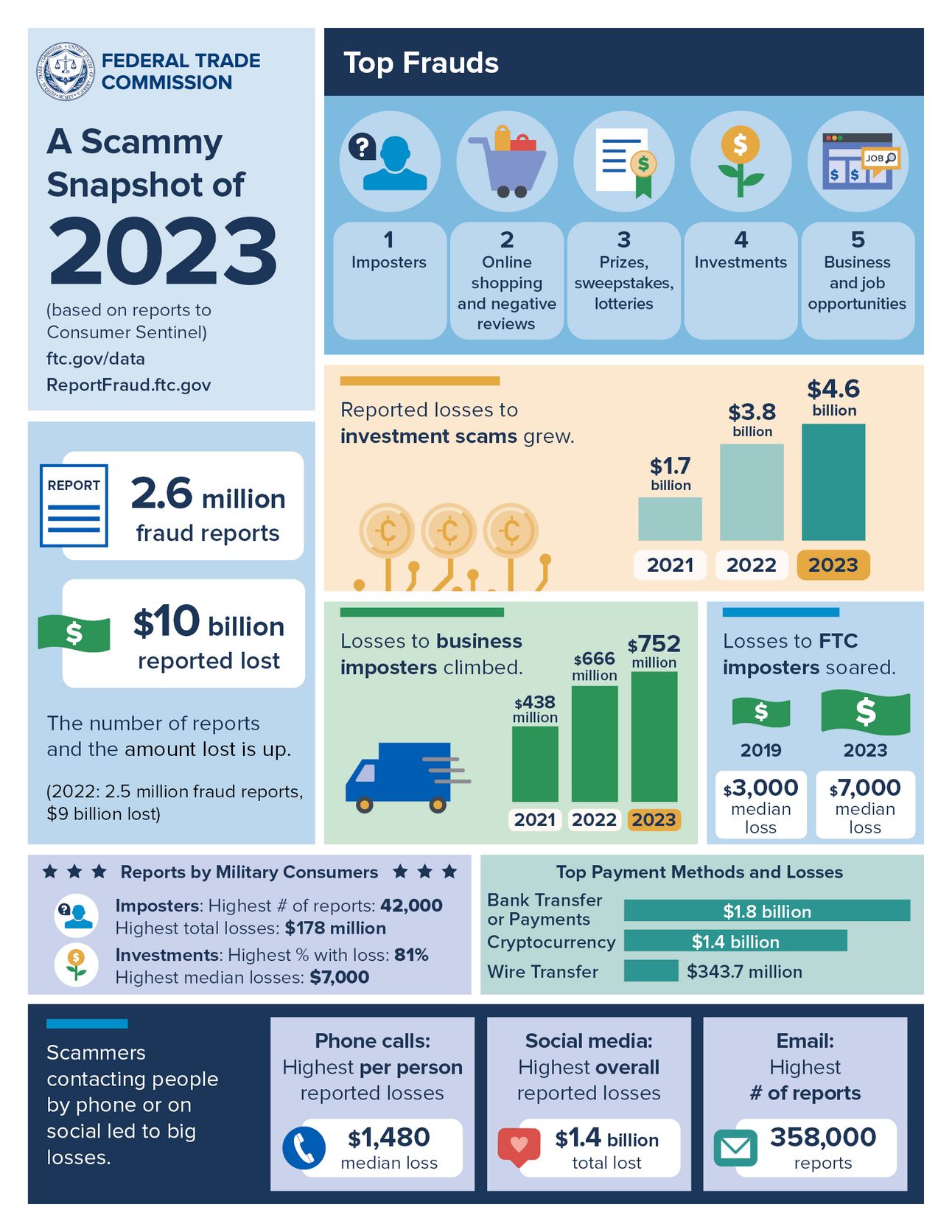
From FTC’s press release
As deep fake technologies advance and cybercriminals adopt them into their workstreams, these scams are only likely to continue to grow in frequency and likely total dollar losses.
This brings us to the next section…
Deep Dive
Deep Fakes Are Getting Us In Deep Trouble

Reports of attackers using deep fakes in attacks are picking up steam. As a reminder, a deep fake is a GenAI-created image, voice, or video that appears real but is artificially created…just ask Taylor Swift about the devasting impact this can have on individuals. It’s terrifying and disgusting what people on the Internet will do.
There’s one other headline that made waves. Scammers used a deep fake video conference to steal $25.6 million dollars from a company in Hong Kong.
But, like most stories, there’s more to it than just the headlines. I dug up the original story to get the full scoop. Here’s how the scammers pulled off this digital heist:
The scammers sent a phishing email to up to three finance employees in mid-January, saying a “secret transaction” had to be carried out.
One of the finance employees fell for this phishing email. This led to the scammers inviting the finance employee to a video conference that included what appeared to be the company CFO, other staff, and some unknown outsiders. This was the deepfake technology at work, mimicking employees’ faces and voices.
On the group video conference, the scammers asked the finance employee to do a self-introduction but never interacted with them. This limited the likelihood of getting caught. Instead, the scammers just gave orders from a script and moved on to the next phase of the attack.
The scammers followed up with the victim via instant messaging, emails, and one-on-one video calls using more deep fakes. This applied more pressure and presumably gave specific instructions for the next step.
The finance employee then made 15 transfers totaling $25.6 million USD to five different bank accounts.
As you can see, deep fakes were a key tool the attacker used, but it was not the only tool. It’s clear that deep fakes can help attackers in social engineering but it’s not yet to the point where it may work standalone.
But…
Things are moving fast in the deep fake space. When I tested building AI-generated audio of my own voice several months ago, I used 90 seconds of my voice. And it just wasn’t believable (or at least I hope I don’t sound like that).
Fast forward to January this year, and Microsoft is saying that with their new VALL-E (X) language modeling approach for text-to-speech synthesis (TTS), they can generate high-quality personalized speech with only three seconds of a speaker’s voice.
Thanks, Microsoft…
So what can you do about this? For businesses and everyday people (yes, you), it can seem pretty frightening. The good news is that security basics are still your best friend.
Trust your gut. The finance employee in this example reported a “moment of doubt” but went forward with the money transfer anyway. If something doesn’t feel right, slow down and...
Validate! Extra emphasis needs to be placed on verifying the authenticity of requests. Using out-of-band authentication with a known and trusted contact method is critical. A 30-second call to verify a request can save your company millions.
On the personal side, scammers prey on people’s desire for quick money or fear of something going wrong. If something pops up out of the norm, step back and think about the situation. Ask clarifying questions and seek legitimate ways to flush out the truth.
News
What Else is Happening?
🧼 Clorox’s most recent earnings report called out $49 million dollars of added expenses in the second half of 2023 due to their cyber attack. They specifically highlighted costs related to forensics, IT recovery, and other professional services required to remediate the attack. This also includes additional operating costs that resulted from the business disruption.
👮 The FBI isn’t backing down from the fight against the operators of the Hive ransomware group. After a disruption campaign that took down the group's servers in January 2023, the US Department of State is offering a reward of up to $10M for information leading to the identification of individuals holding a leadership position in the Hive ransomware group. They’re also offering up to a $5M reward for information leading to the arrest or conviction of any individual conspiring to participate in Hive ransomware activities.
🔑 Researchers at SpiderLabs found attackers using fake job advertisements on Facebook to spread the Ov3r_Stealer infostealer. The malware targets data for crypto wallets, Discord, browser extensions (including password managers), and various documents (text, excel, and Word documents). This is just one more of the infostealers out there plaguing users and businesses alike.
If you enjoyed this, forward it to a fellow cyber nerd.
If you’re that fellow cyber nerd, subscribe here.
See you next week!

