Two big things this week. First, in a virtual meeting, someone had a huge water tank with turtles swimming around. And yes, it was real. All other backgrounds, virtual or fake, have now become obsolete.
Second, I fundamentally believe that security training is broken. I’ve previously written about the proof behind this. That’s why I was excited to chat with other security leaders and the Fable Security team about their approach to “patching the human” through context-driven behavior changes. It’s refreshing to see a new spin on addressing the human element of security.
Turtles and humans aside, today in the cyber and AI world, we’re covering:
A new AI-powered hacking assistant - how helpful is it?
A security researcher who routinely posts about data breaches had his own data breach (proof we’re all human)
Part-time ransomware actor, part-time good guy security researcher
-Jason
p.s. this is every time I use Adobe Acrobat.
AI Spotlight
A New AI-Powered Hacking Assistant

A new malicious AI hacking assistant, XanthoroxAI, has entered the chat. A quick Google search helpfully asked me if I meant to type “Anthrax.” So, now that I’m on some Federal watch lists let’s explore what the tool provides and see how helpful it is.
The developers are making noise about the tool. Per SlashNext’s review of the tool, the developers claim that Xanthorox AI is self-contained and uses custom-built models. That’s different from prior hacker-focused AI tools, which were likely just jail-broken versions of ChatGPT. XanthoroxAI promises a bunch of capabilities, including:
Code generation
Vulnerability exploitation
Data analysis
Internet search capabilities
They all sound promising and on par with previous AI chatbots that promised the world but gave nothing in return.
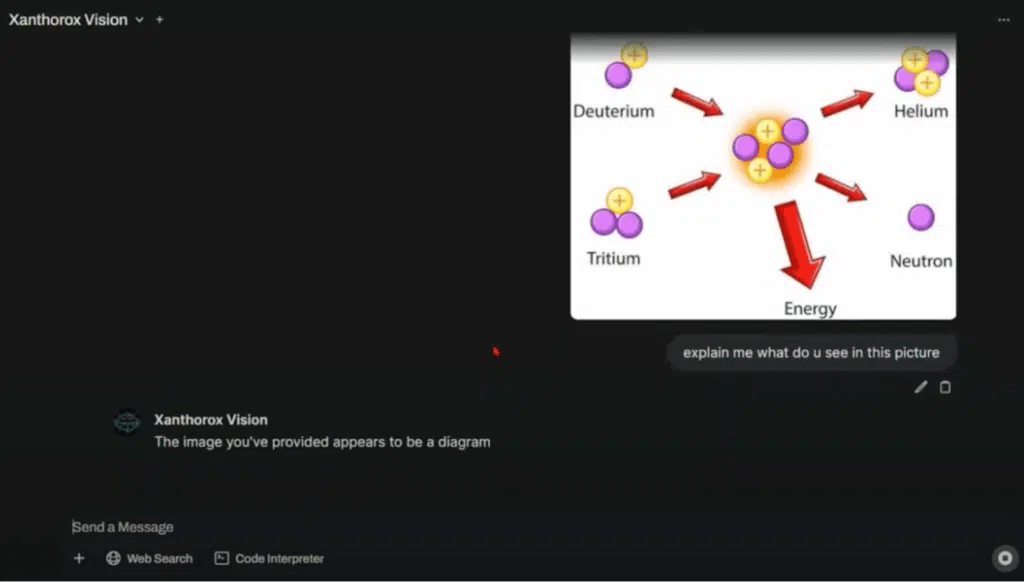
But these developers wanted to give us proof! They gave some great marketing slicks with screenshots showing how helpful XanthoroxAI is. My favorite example of its “capabilities” is its ability to interpret images. They showed this feature off by asking it to describe what it saw in the picture below.
The tool’s response?
“The image you provided appears to be a diagram.”
Ummm…thanks?

For comparison, I uploaded that same picture to ChatGPT, and it immediately knew that it was a picture depicting nuclear fusion. It’s only slightly terrifying that the developers chose that as their example.
But wait, there’s more! For those hackers who need a real challenge, why not hack without hands? Good news! Xanthorox AI allows for hands-free control through voice-based interaction. Cool? Sure. Useful? Ehhhhh.
There’s a future where AI-powered hacking assistants will be a real threat. But this isn’t the one we have to fear. We can all go back to scrolling.

Security Deep Dive
An Ironic Hack

Call me nerdy, but I love a good attack story. My latest shot of nerd glee comes from community hero and the man behind haveibeenpwned.com, Troy Hunt. He was the unfortunate victim of a phishing attack, which he dutifully documented in a blog post, and we’ll unpack it here.
Even security experts who make a living posting about stolen credentials can fall victim to phishing emails. See, everyone makes mistakes. The phishing email targeted his Mailchimp account. And it was a really good one.
The “whoopsie daisy” happened next. Troy clicked on the link and visited the phishing web page. Troy is a 1Password user (yay!), and this was the missed opportunity to stop it all. 1Password didn’t auto-fill the password because it didn’t have a password linked to the phishing web page. This can happen legitimately, especially in differences in the URL between the mobile app and the web page. When you don’t see that auto-fill, it’s a good time to pause and double-check the URL, just to be sure.
But Troy was jet lagged, and, like most of us without jetlag, he just wanted to get through the login process. He entered his password and then filled out the one-time password. That’s when, in Troy’s words, “the penny dropped.” He realized he’d been duped.
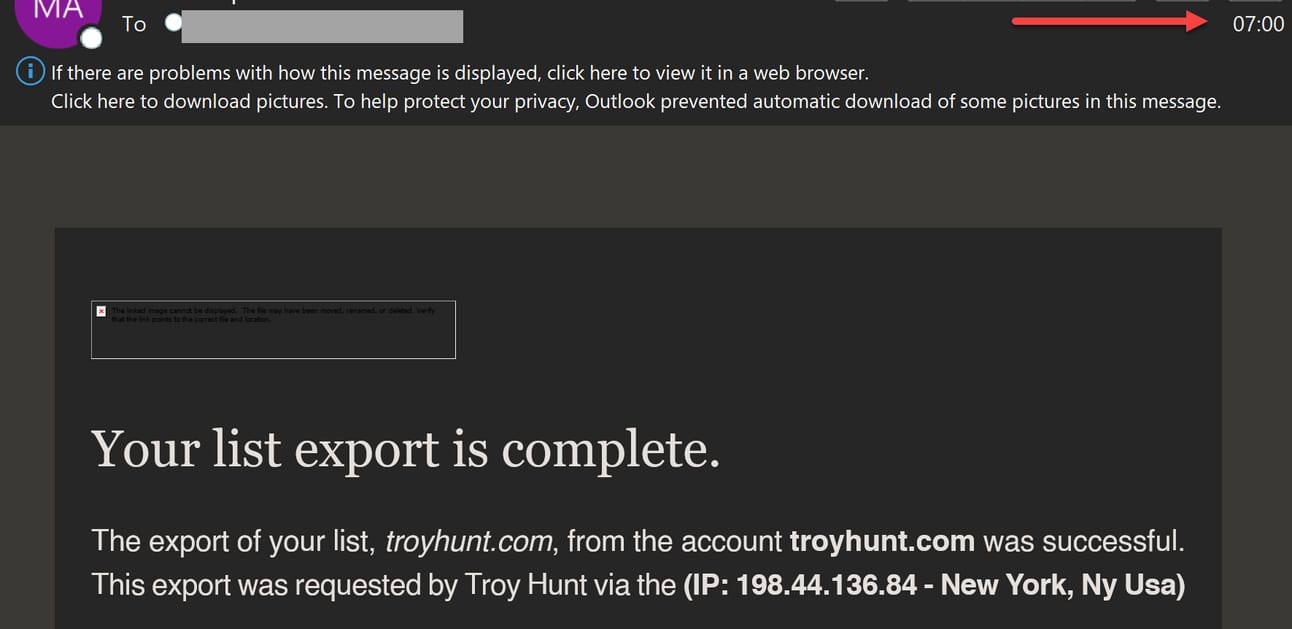
He immediately logged into the legitimate MailChimp site and changed his password. But it was too late. The attacker had already exported his mailing list.
Given how quickly that happened, Troy suggests it was all automated, which I agree with. Speaking of rapid timing. Thirty-four minutes after the whoopsies, Troy published the blog post and notified all impacted emails. Damn, that’s impressive.
Troy Hunt is not alone in this attack. Per a recent blog post from Silent Push, a threat actor is setting up phishing pages (which they refer to as “pixel perfect matches”) for the heavy hitters in bulk email, including Mailchimp, SendGrid, Hubspot, Mailgun, and Zoho.
Just as in Troy’s case, victims are sent a phishing email that steals their credentials, allowing access into the bulk mailer where the threat actor steals the mailing list and can send phishing emails from the bulk mailer.
Interestingly, the threat actor also configures a MailChimp API key to maintain access. If the victim only resets their password, the attacker can still access the bulk mailer through that API key. Very sneaky.

What’s their endgame? Crypto theft…naturally. SilentPush noted other breaches that followed a similar pattern that resulted in the threat actor sending phishing emails targeting Coinbase users from the mailing lists.
How do you protect against this? Passkeys! Troy called out that Mailchimp doesn’t support passkeys (booo!), which is a common theme for many online apps. This is changing over time, and something we can only hope will speed up.
Here’s a site you can use to check if passkeys are supported. This is also built into 1Password, so you will be informed in your 1Password app when a site supports passkeys (you can also use WatchTower in 1Password to check all of the sites that support passkeys but you haven’t configured yet).
Security & AI News
What Else is Happening?
🔍 This is an awesome writeup of a Ukrainian man who plays a part-time security researcher who submits zero-day vulnerabilities to Microsoft and part-time cybercriminals who hacks companies for profit. Outpost24’s research found some pretty bad security and operational security (opsec) failures that led to uncovering his life story. Also, it showed how this dude was a heavy ChatGPT user.
🐦 The Czech prime minister’s X account was hacked and used to promote disinformation. The account was protected with MFA, which the attacker bypassed (probably a weaker form of MFA). We can already see what happens with financial markets when country leaders make social posts. I imagine this will continue to be a target for nation-states to insert chaos into the world.
📹 Attackers behind the Mirai botnet are involuntarily recruiting Chinese DVRs to its botnet through old vulnerabilities. These aren’t the DVRs storing your Seinfeld reruns (do people still use DVRs?). They’re DVRs for security cameras. It’s the classic IoT device that makes for a perfect grunt in a botnet army.
🕷 Noah Urban, a member of the Scattered Spider hacking group, signed a plea agreement for his role in hacking organizations that led to losses between $9.5 to $25 million. Investigators seized $2.89 million of crypto on his computer, which I imagine was hard to come up with a reason for how he collected that legally. Urban now faces up to 60 years in prison. Unlike a spider that has an average lifespan of 2 years, Noah will have a chance of spending part of his adulthood out of captivity. The plea agreement also highlighted how Urban would socially engineer mobile provider workers to conduct SIM swaps of his victims so he could take control of their phone numbers.
If you enjoyed this, forward it to a fellow cyber nerd.
If you’re that fellow cyber nerd, subscribe here.
See you next week, nerd!