Good morning and happy holidays! While I’d like to say this is a special holiday edition, it isn’t. BUT, the events of this week took me down hours-long rabbit holes into the tech behind what many think of as the dark web. So, follow me on my journey and reap the rewards of what I found.
Today we’re covering:
The epic BlackCat/ALPHV vs FBI showdown…who will win?
The tech behind the dark web (or at least some of it).
A record week for impacted individuals from data breaches?
-Jason
Spotlight
The BlackCat/ALPHV Drama

On December 19th, the US Justice Department announced the results of a “disruption campaign” against the BlackCat/ALPHV ransomware group. This is a particularly nasty group, with over 1,000 victims and $300 million USD in ransom proceeds.
The disruption campaign involved the FBI taking control of the group’s leak site on the dark web. Attorney General Lisa O. Monaco said:
“In disrupting the BlackCat ransomware group, the Justice Department has once again hacked the hackers”
So, how did they “hack the hackers?”
Sneaky Sneaky, FBI

The FBI first found a Confidential Human Source (“CHS”). It appeared to be someone they knew, as the search warrant stated it was someone “who routinely provides reliable information related to ongoing cybercrime investigations.”
The CHS then applied to become a BlackCat/ALPHV affiliate. An affiliate is someone who simply uses the services of the ransomware operation. In essence, they are the real attackers who deploy the ransomware whereas BlackCat/ALPHV is just running the infrastructure to support the extortion part of the attack.
After an interview, BlackCat/ALPHV granted access the CHS access to the ransomware group’s affiliate panel. The FBI obtained another search warrant to explore the portal and determine how the operated. This panel is where affiliates manage their victims, negotiation discussions, and payment details. This panel exists as a Tor .onion site (more on that in the next section).
While it’s not clear how the FBI escalated this access, ultimately they gained access to infiltrate the ransomware group’s network. From there, the FBI collected 946 public/private key pairs. Each BlackCat/ALPHV victim received their own Tor .onion address to access, so this equates to 946 ransomware victims.
On December 10th, the BlackCat leak site went down. The group claimed it was a hardware failure, but rumors flew that it was a law enforcement takedown. Nine days later, on December 19th, the FBI “seized” the group’s primary leak site and redirected users to a splash page showing the site had been seized confirming those suspicions.

Screenshot via @AlvieriD on X
BlackCat/ALPHV Retaliates
The ransomware group didn’t take kindly to this action. Approximately three hours after the FBI seized the leak site, the BlackCat/ALPHV operators “unseized” it…with a threatening message…
The ransomware group told their affiliates that they could now attack any entity outside of the Commonwealth of Independent States (CIS) (which includes Russia). This removed prior rules that blocked attacks against critical infrastructure, including hospitals and nuclear power plants.
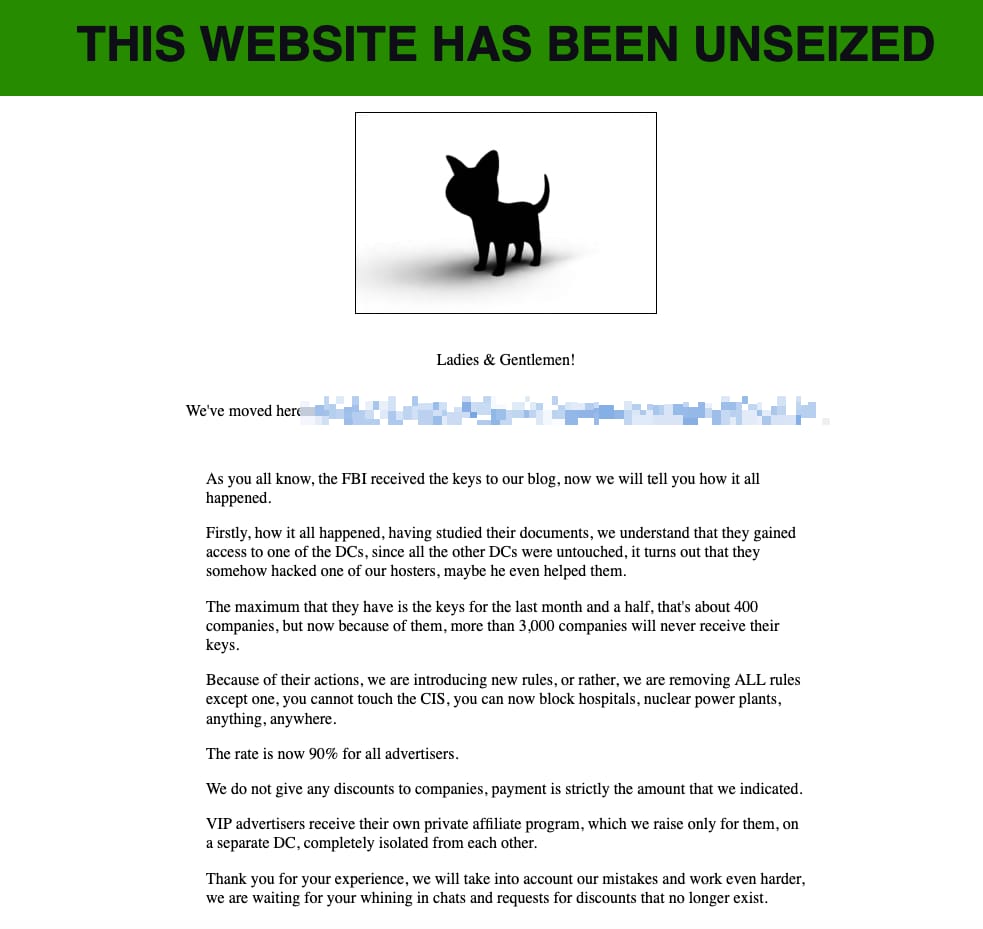
Screenshot via Kevin Beaumont
The fight over the leak site between the FBI and the ransomware group continued. The FBI seized it again with the ransomware group “unseizing” it. Meanwhile, LockBit (the most rampant ransomware gang) and BlackCat/ALPHV discussed joining forces to form a cartel. What a time to be alive…
While all of the headlines were focused on the “tug-of-tor” (har har har), I became fascinated with understanding how the back and forth of the leak site could happen…so I dug in deep to understand it.
Keeep reading to find out how…
Deep Dive
The Ins and Outs of Tor Onion Sites

My research led me to one conclusion. There is one specific issue that led to the table tennis match for the leak site.
It’s about to get nerdy here, so take a sip of coffee and let’s do this!
Where Do Leak Sites Live?
Like most ransomware leak sites, BlackCat/ALPHV’s leak site was hosted on an Onion Service (also known as a Tor Hidden service.) An Onion Service is, quite simply, a web page. But it is only accessible through the Tor network. This is the “dark” part of the dark web because it’s not accessible through the Clear Web, which is where most sites we all access live.
Tor, which stands for The Onion Router, is free and open-source software that allows for anonymous communication over the Internet. This is why cybercriminals favor Tor and why ransomware leak sites can operate from the safety and anonymity of an Onion Service.
To access an Onion Service, you can use Tor Browser to connect to the Tor network. Then, you enter an onion address, which consists of 56 letters and numbers followed by “.onion,” into the URL bar to connect to the Onion Service. As an example, the onion site for the CIA (no joke) is:
ciadotgov4sjwlzihbbgxnqg3xiyrg7so2r2o3lt5wz5ypk4sxyjstad.onionAnonymity for the Tor network lies in how you connect to systems. It’s not a direct route from your computer to your destination. It jumps through a circuit (or pathway) of at least three Tor nodes (relays). These are just computers running the Tor software. Using Tor Browser, you can anonymously connect to normal websites like Google, as seen below.
This makes it so that the client (person using Tor browser) and the end destination (e.g. a legitimate web page like google.com) don’t know each other. The middle relay anonymizes everything.

Now the above happens when you use Tor to access sites on the clear Web. When we’re talking about Onion Services, which only live on the Tor network, something different happens.
When the client connects to an onions service, a circuit of six hops is created. To understand why, let’s explore how Onion Services are created and how clients connect to them.
How Onion Services Are Created
Let’s assume an attacker wants to create a leak site as an Onion Service. They first install Tor on a server and configure a web service to run on that server.
A small configuration tweak to Tor’s configuration file then tells Tor the folder on the server that contains the webpage and a key pair (private and public key) used to authenticate and encrypt traffic to the Onion Service (this creates end-to-end encryption, even more security).
Onion Service Configuration
Here’s a high-level summary of what happens behind the scenes:
The Onion Service generates a key pair, which includes a private key and a public key. This is critical to understand. The public key is distributed to clients, which are people who want to visit the Onion Service. The private key stays on the server and is the primary mechanism to show “ownership” of the Onion Service.
The onion address is then created by base32 encoding the public key, a checksum, and a version number together. The “.onion” suffix is added to the end.
The Onion Service selects three random Tor nodes (other systems running Tor) as introduction points for the Onion Service. Introduction points help coordinate the connection between clients and the Onion Service.
The Onion Service then creates an Onion Service Descriptor. This file includes the three introduction points and the public key. The Onion Service Descriptor is signed with the private key, which is later used to authenticate that clients are connecting to the right Onion Service.
The Onion Service then uploads the Onion Service Descriptor to a distributed hash table, which is part of the Tor network. This is how clients are able to find the Onion Service.
At this point, the leak site would be available to anyone who wants to connect, as long as they know the onion address.
Now let’s see what happens when someone tries to connect to the Onion Service.
How Clients Connect to Onion Services
A user launches Tor Browser and enters the onion address.
The client downloads the Onion Service Descriptor from the distributed hash table. The client verifies the signature from step #4 with the decoded public key. If successful, it shows that this is the right server to connect to and is trusted. This is because it only assumes only the valid server has the private key.
The client picks a random Tor node as a rendezvous point.
The client connects to one of the three introduction points and provides the location of the rendevous point.
The introduction point provides the client with a unique one-time secret and tells them to wait for the onion service at the rendezvous point.
The introduction point then connects to the Onion Service and tells them to meet the client at the rendevous point. The introduction point gives the same one-time secret to the Onion Service so they know to talk with the right client.
The client and the Onion Service both create a circuit to the rendevous point (hopefully the name makes sense now). As seen below, the client picks three Tor nodes (with the third being the rendezvous point), and the Onion Service picks three other Tor nodes for a total of six nodes. This maintains complete anonymity between the client and the server running the Onion Service.
After meeting at the rendezvous point, the client and Onion Service compare the one-time secret. If it matches, they begin communicating with each other, and the client loads the web page (e.g. a leak site) hosted at the Onion Service.
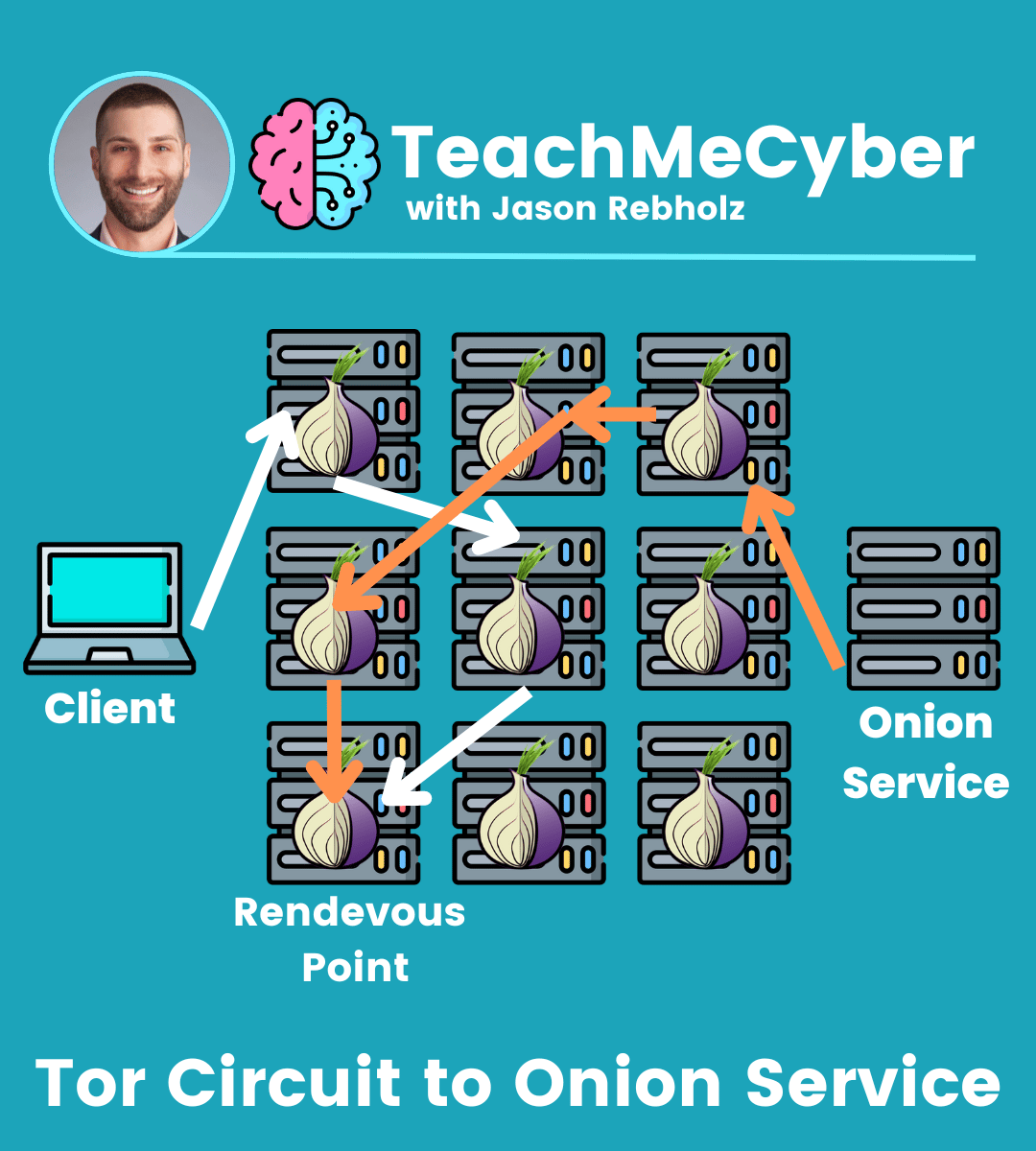
This can be pretty complicated, so hopefully I did it some justice here. If you really want to nerd out, here are technical specs on everything.
The Lesson
Leak Site Tug-of-Tor
So, going back to the main question. How is this battle for where the leak site points to happening in the first place? In other takedowns on the Clear Web, you don’t usually hear of this activity.
I casually hinted at the answer in the description above. The key to BlackCat/ALPHV taking back control of their leak site comes down to the private key!
Because law enforcement simply copied the key, both parties have the private key. As we learned in the Onion Service configuration, whoever has the private key can push out an updated version of the Onion Service Descriptor and direct users to their server.
There is no way to stop this because the private key is the only thing that “proves” ownership over the leak site. Both parties can continue to publish a new Onion Service Descriptor file on their own servers. Whoever is the last person to publish, wins.
It’s likely that the ransomware group will give up on the game and let it go because there is no point in continuing. No affiliate is going to want to use the old site. In fact, this is likely the start of a slow death to BlackCat/ALPHV because trust has been eroded.
The threat intel firm Redsense has a great blog post on how law enforcement actions break down ransomware groups. I highly recommend this read.
News
What Else is Happening?
A ton of breaches, that’s what…
📺 Attackers used the Citrix Bleed vulnerability to hack into Xfinity. Information for over 35 million people was impacted. This included usernames and hashed passwords, and for an unknown number of individuals contact information, date of birth, secret questions/answers, and the last four digits of their social security number.
🏠 Mr. Cooper, a massive mortgage lending firm, gave an update to their October security incident. 14.7 customers of Mr. Cooper (including me) had their data stolen. This included full name, address, SSN, date of birth, and bank account number. If you’re impacted, freeze your credit now!
🎄Hackers ruined Christmas. In an SEC filing, VF Corp (the company behind The North Face, Vans, and Timberland - among others), was hit with a ransomware attack. They stated that while customers can make orders, fulfillment was impacted, which, given the timing, could impact holiday shipping.
Wow, this was a long and nerdy post today. If you made it this far, congratulations, you get extra nerd points.
Reply to this and let me know if you liked this deep dive format. It was a ton of extra work but also extra rewarding to be able to go deeper on a single topic. I’d love to know if it resonated with you.
See you next week!

