The Weekend Byte is a weekly overview of the most important news and events in cybersecurity and AI, captured and analyzed by Jason Rebholz.
Let’s start this off with some feel-good things. Like the finalists in the Nikon Comedy Wildlife awards or a new social media app that gives you as many AI followers as you want, complete with comments and trolls. Umm, wait, on second thought, I’ll stick with the funny animal photos.
Today, we’re covering:
AI-enabled malware
Hold my CUPS, a new doomsday vulnerability?
Grief tech industry…helpful or creepy?
-Jason
Together with NordPass
“Password” and “123456” are some of the most popular passwords breached across Fortune 500 companies.
Try NordPass to create, store, and share passwords and credentials safely. Use my code “weekendbyte” to get a free 3-month trial or 20% off NordPass Business. Check it out here.
AI Spotlight
Malware + AI Sitting in a Tree, K-I-S-S-I-N-G

F’ing Infostealers. They’re everywhere now. And not being content on just dominating the malware ecosystem, they’re also experimenting with using AI.
Enter stage left, Rhadamanthys (say that five times fast and then proceed). Per a RecordedFuture report, it first appeared in 2022. Like a cast member of Selling Sunset, it had a lot of work done it since coming onto the scene, with at least ten different updates in the last two years!
It does what any good infostealer does: steal system information, passwords, cryptocurrency wallets, and cookies. But why stop there?
The latest feature of the Rhadamanthys infostealer adds a bit of AI to the mix with a new feature called “Seed Phrase Image Recognition.”
Seed phrase? A seed phrase is a sequence of random words that store the data required to access or recover cryptocurrency on blockchains or crypto wallets. Its primary use case is in recovering inaccessible crypto wallets if you’re a legitimate user who happens to get locked out or lose your wallet. If you’re a malicious person, you can use the seed phrase to steal someone’s crypto.
Now, back to the infostealer. The new function works by first searching the system for images and doing a cursory check to see if seed phrases are present in the image. If that checks out, it ships the file to the attacker’s server to process through an open-source Optical Character Recognition (OCR) engine to more accurately find and extract the seed phrases.
OCR has been around for a while. While it is AI, it’s not the use-case many think of when they think of “AI-powered malware.” Either way, it’s a pretty cool tactic that spells more danger for the average user.
Meanwhile, HP’s Wolf Security team spotted a new thing. They found scripts used to infect systems with Async RAT (a backdoor) that appeared to be created with GenAI. They’re basing this on the structure, comments, and specific language used in the script. While not 100% certain, it wouldn’t be surprising if attackers did use it to support building scripts to infect systems.
Security Deep Dive
More Internet Drama Critical Vulnerabilities

This week’s cyber doomsday vulnerability Internet drama started on Monday when a security researcher chose violence…

Now, in all fairness, he tried to do the right thing. He just chose colorful language…
Matters were made worse when the original agreed-upon disclosure date of October 6th was sped up to September 26th because the report was leaked on a hacking forum.
Then, the media picked this up and gave it the doomsday title because rhetoric always finds a way to intensify.
So, how bad is this? You have to look at this in two ways. First, how many of these systems are running the service that is Internet accessible? This means a remote attacker can exploit the vulnerability.
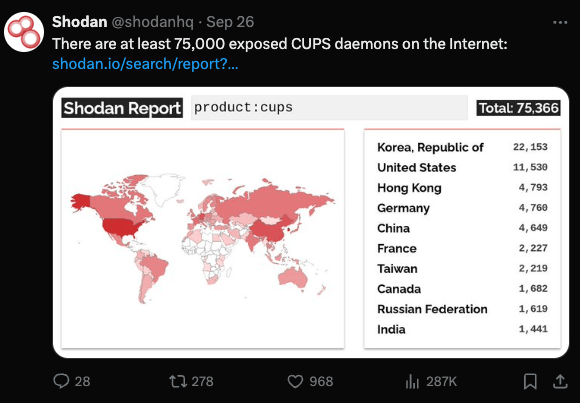
There are many different numbers floating around. The security researcher who found the vulnerability sees around 68K Internet-accessible systems, while Shodan reports about 75K. Many of which seem to be connected to telecom and hosting providers.
The second way to look at this is any Linux system running the vulnerable service. Attackers who have already gained access to a victim’s environment can scan for local servers running the software and attempt to exploit them. This is less severe because it requires an attacker to be on the same local network, meaning they have already hacked into a network.
Okay, cool. What’s the vulnerable software? The vulnerability impacts Linux systems running CUPS. While the CUPS service won’t hold a delicious beverage for you, it will help direct print jobs to printers for you. Who knew that a service that does something as boring as routing printer jobs could become so popular?
The vulnerability works like this:
1. The attacker connects to the CUPS service and directs it to connect to an attacker controlled server, which tells the vulnerable service that it’s a printer.
2. The attacker controlled server returns information about the “printer.” This can include commands to execute on the vulnerable server. This is why it’s bad. An attacker could include malicious commands to take control of the system or download malware.
3. When a print job is sent to the vulnerable system, the newly added printer with the malicious commands, are executed on the Linux system.
While the vulnerability is bad, it won’t impact most organizations. That’s because the vulnerable service the attacker must connect to is not typically accessible to the Internet. A company would have to go out of its way to make it so.
It’s still important to patch your systems quickly because you don’t need this vulnerability lying around. But we can take a collective breath that we’re not dealing with the next Armageddon vulnerability.
Security News
What Else is Happening?
🔐 In July, Chrome released a new feature to protect against infostealers taking cookies from users’ cookie jar browser. Fast forward to today, and infostealers have already found a way around Google’s weak attempt to keep attackers’ hands out of the cookie jar.
🗒 What happens when you compile emails from many public data breaches and then remove duplicates? You create a list of 3.3 billion email addresses. Maybe that hacker needs to find a hobby.
🔎 US Senate security officials warned lawmakers to be on the lookout for deepfake video calls. This followed a Zoom call between Ben Cardin, the head of the Senate Foreign Relations Committee, and someone purporting to be a top Ukrainian official. Senator Cardin became suspicious after a series of weird questions.
🤔 I’m not sure how I feel about the grief tech industry…an entire industry that builds AI copies of people who have passed away.
🇺🇦 Ukraine’s cyber agency reported that “hackers are no longer just exploiting vulnerabilities wherever they can but are now targeting areas critical to the success and support of their military operations.” In other words, they’ve shifted from attempting to create chaos and destruction to persistent access that facilitates strategic objectives.
🧳 Telegram updated its policy to share phone numbers and IP addresses with law enforcement, which is causing cybercriminals to find alternatives for communication or bolster their knowledge of how to stay private on Telegram.
If you enjoyed this, forward it to a fellow cyber nerd.
If you’re that fellow cyber nerd, subscribe here.
See you next week, nerd!