Good morning! I spent a few days in Boston this week for annual planning. Some people hate it. I thrive on it. As I do it, I always think of this quote from Dwight Eisenhower:
Plans are nothing; planning is everything.
The act of planning helps clarify your thoughts and direction. The plans can and will change, but the process of thinking through things clearly and long-term is invaluable.
But I digress…today in cyberland, we’re covering:
Escalations in the cyberwar between Russia and Ukraine.
A new, secret underground marketplace for hackers.
The worst employee ever.
-Jason
Spotlight
Ukraine and Russia’s Cyber War Escalates

The cyber war between Ukraine and Russia is escalating…and quickly. On Tuesday, Ukraine made a public statement claiming they hacked Russia’s Federal Tax Service (FNS) and a Russian IT company that served Russia’s FSB.
Whodunnit?: While many nation-state cyber operations happen constantly, it’s rare to see one take credit for it. In this case, the Main Intelligence Directorate of the Ministry of Defense of Ukraine not only took credit but bragged about it too, commenting that Russia has “been unsuccessfully trying to restore the work of the Russian tax authorities for the fourth day in a row.”
Not Their First Rodeo: This is the same group that hacked Russia’s Federal Air Transport Agency back in November and stole a large amount of data. The stolen data suggested that Russia’s civil aviation is “on the verge of collapse” due to increasing mechanical issues with their planes and difficulties in repairing them due to parts shortages from sanctions and lack of skilled labor.
So No More Taxes?: As part of the cyber operation, Ukraine deleted the core FNS database, critical configuration files, and all of their associated backups. They claimed that they deployed malware to over 2,300 servers. Although the functionality of the malware was not clear, Ukraine’s message suggested it was wiper malware that made the systems inoperable.
Russia’s Response: Russia didn’t take this sitting down. The same day that Ukraine went public with its hack, Ukraine’s largest mobile network provider, Kyivstar, was the victim of a cyber attack. While Russia hasn’t claimed responsibility, it’s widely suspected that Russia was behind the attack…because we’re not idiots.
Even though the new leader of Killnet is claiming responsibility.
Source: Killnet Telegram Channel
The cyber attack impacted mobile services for 24.3 million Ukrainians. That’s more than half of the Ukrainian population. This also impacted merchants all over the country as they were unable to process credit card payments and ATMs stopped functioning.
The CEO of Kyivstar, Oleksandr Komarov, said “It’s an enormous hit on the infrastructure.” The company was forced to physically disconnect Kyvistar from the network to try and contain the damage. Thankfully, the company made short work of restoring their operations, having fully recovered mobile internet by Friday.
A History of Russian Hacks: This is just one more hack that Russia has targeted against Ukraine since the invasion. Many of which were destructive in nature. The largest of which was the hack against Viasat the day Russia invaded Ukraine. That cyber attack bricked thousands of Viasat modems.
Looking Forward: It won’t be surprising if this tit-for-tat continues between Ukraine and Russia. Each side looks to cause more pain and embarrassment with each digital swipe. Let’s just hope it doesn’t spill out beyond the borders or translate into a humanitarian crisis.
Deep Dive
Holiday Discounts for Hackers

Gif by schittscreek on Giphy
Where do you shop for a hacker that has it all? An underground marketplace of course! A recent Zerofox report shed light on a new up-and-comer in the space, known as OLVX.
Not So Secret: Unlike most dark web marketplaces, OLVX isn’t afraid of the light and lives on the open web. This means that anyone can access it using any browser, it just requires you to register an account. While convenient for newbs less skilled users looking for illicit goods, it does pose a challenge for keeping it online. Just last week, the original domain was taken over (unknown if it was a rival or law enforcement), and they were forced to change their domain to maintain operations.

Source: OLVX Telegram channel
Building a Following: Growing an online business is difficult, and it’s even harder if you’re doing something illegal. To expand their footprint, the operators of OLVX use search engine optimization (SEO) techniques to capture keyword searches and bump up the list on Google search results. They also use other traditional marketing methods, like advertising on other forums, Telegram, and good old-fashioned word of mouth.
Of course, some holiday discounts don’t hurt either with the marketplace advertising a Christmas sale.

Source: OLVX telegram
What’s for Sale? Like any good marketplace, OLVX offers a lot of different goods. From access to compromised systems and accounts to various hacking tools. Popular goods include:
Web Shells: Provide access to compromised websites/servers
cPanels: Access to a website’s administrative panel
Phish Kits: Automate phishing and MFA bypass techniques
Remote Access (RDP and SSH): Compromised server logins, including RDP access tied specifically to hosts in Azure.
Webmail Accounts: Compromised email credentials for a variety of different hosting providers.
Website Accounts: Compromised creds for various online sites…including dating sites for those hackers feeling lonely this holiday season.
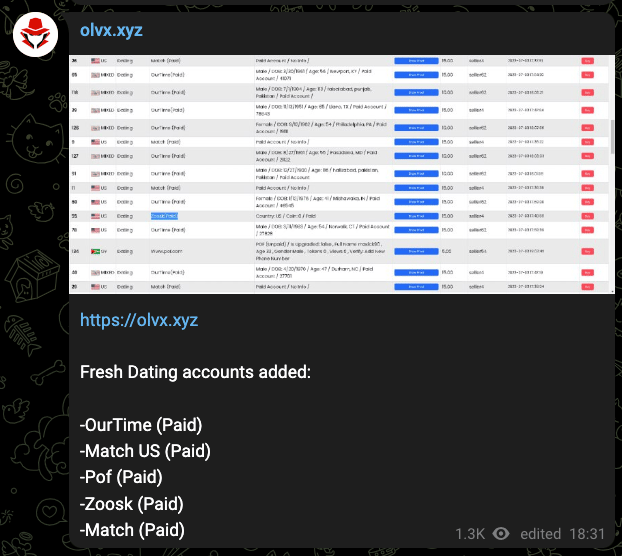
Source: OLVX telegram
News
What Else is Happening?
☁ A former cloud engineer at First Republic Bank was sentenced to two years in prison for wreaking havoc on the company. After being fired for cause, the employee logged into the systems later that evening, before his access was cut off, and deleted the bank’s code repos, deleted logs, and left taunts in computer code.
🧟 🦆 The Microsoft Threat Intelligence saw the resurgence of Qakbot in a small phishing campaign that began on December 11. This followed a law enforcement takedown of the infrastructure in August 2023. Maybe it’s just me, but when I see Qakbot, I see “quack.” Could this be the first documented case of a zombie duck?
🤙 Abnormal Security spotted a new BazaCall campaign that uses Google Forms to trick users into thinking there was a fraudulent purchase in their name. The only instructions are to call a phone number to stop the purchase. This leads to an actual human who then tries to trick the victim into installing malware on their system, which will lead to actual fraud.
🔑 Threat Intel company HudsonRock, is seeing attackers setting their targets on password vaults. They gain credentials via infostealers, brute-forcing, or from other data dumps where users reuse passwords. This should go without saying, but please use phishing-resistant MFA on your password vaults.
See you next week!

