I spent a lot of time this week in deepfake wonderland testing different synthetic audio and video services that are available. It was a defining moment for me to see how easy it is to do. It’s a problem space I look forward to continuing to learn more about, so I hope you’re ready to take the trip with me.
We are stepping into a future where we really won’t know what is real. One can only hope they still have delicious snacks there.
Speaking of delicious snacks, this week’s cyber dumplings 🥟 include:
Interview with a
vampireteenage social engineering millionaire.Lockbit exposed?
From text messages to unauthorized online bank withdrawals
-Jason
Spotlight
I’m Sorry, You Make How Much?
I’m getting the feeling that screen time is not the only thing we have to worry about with teenagers. I listened to a crazy recorded phone call between Juneseth, a crypto nerd, and a high school (yes, you read that right) con artist who went by Daniel. Mr. Daniel tried to steal Juneseth’s crypto assets by socially engineering him, which kicked off a 35-minute discussion on Daniel’s life choices.
His life of crime started with video games. When Daniel was at the young and impressionable age of 13, he met a group of Minecraft enthusiasts who hung out in real life and the Minecraft block world. It was there that stranger danger happened…
A random person that Daniel and his friends met in the Minecraft world started to open their eyes to the world of stealing crypto assets by socially engineering people. Trick these peons into handing over their passwords or other sensitive information, and you can steal their crypto assets.
That stranger started to give these teenagers jobs calling targets and tricking them into handing over passwords. After learning how it all worked, Daniel and his friends followed the solopreneur dream once they finished their math homework and took the garbage out.
The scam starts with a list of crypto whales, who are high-net-worth individuals in the crypto space. According to Daniel, these lists are expensive, costing hundreds of thousands of dollars. They then hired Russian programmers to create an auto-dialing program that would call the target victims and get them to accept a call from them by clicking through to connect with a human. This provided them with a qualified lead, which is half the battle.
Once they got on the phone, they used techniques that preyed on greed and fear. They usually pretended to be tech support and were reporting a fake security incident that impacted the victim’s account. To fix everything, the victims were tricked into providing information like passwords or seed phrases, a sequence of random words that store the data required to access or recover cryptocurrency.
Daniel used a classic Google Forms technique to collect this information. This is helpful because the form originates from Google, so it can look legitimate. Once they had the information, they could recover the crypto or transfer it to themselves, then wash the crypto to disrupt any investigations into where it all went.
These kids are making bank. Daniel reported that most of his friends are millionaires, with one having more than $40 million in crypto before he could attend prom. Whether he would find a date is a story for another day.
Daniel hopes to make a few million dollars before “retiring” and become a financial consultant. Oh, and naturally, he wants to buy a penthouse and drive a Ferrari.
These kids are good. Not Santa’s list “good”. I mean good at their job of screwing people over. Their social engineering approach is next level with their native English language capabilities and they just sound personable. It makes it seem legit.
Interestingly, our new BFF Daniel feels almost no remorse for his crimes…at least most of the time. He said that people who gave away this information deserve to lose their assets. We’ll file that as an obvious way to try and justify such disgusting behavior.
He also called out how it didn’t feel like real life. Calling people and stealing so much money felt like a video game to him. Perhaps this is how ransomware actors feel about their faceless crimes.
Later in the call though, when Daniel started discussing his “retirement” plans, he highlighted that he started thinking hard about the impact this would have on people and that it might not be his best career choice.
Well, Daniel, I hope you come to your senses before you ruin your entire life.
Deep Dive
LockbitSupp Hits the Gym

In February, law enforcement seized the notorious Lockbit group’s servers and began an epic troll against the site’s operator, LockbitSupp. Just short of a Drake and Kendrick Lamar diss track, the two opted to send their messages using their respective leaksites.
Law enforcement restored Lockbit’s seized servers last week with a new message. The updated leaksite included more information about the affiliates with a huge surprise.
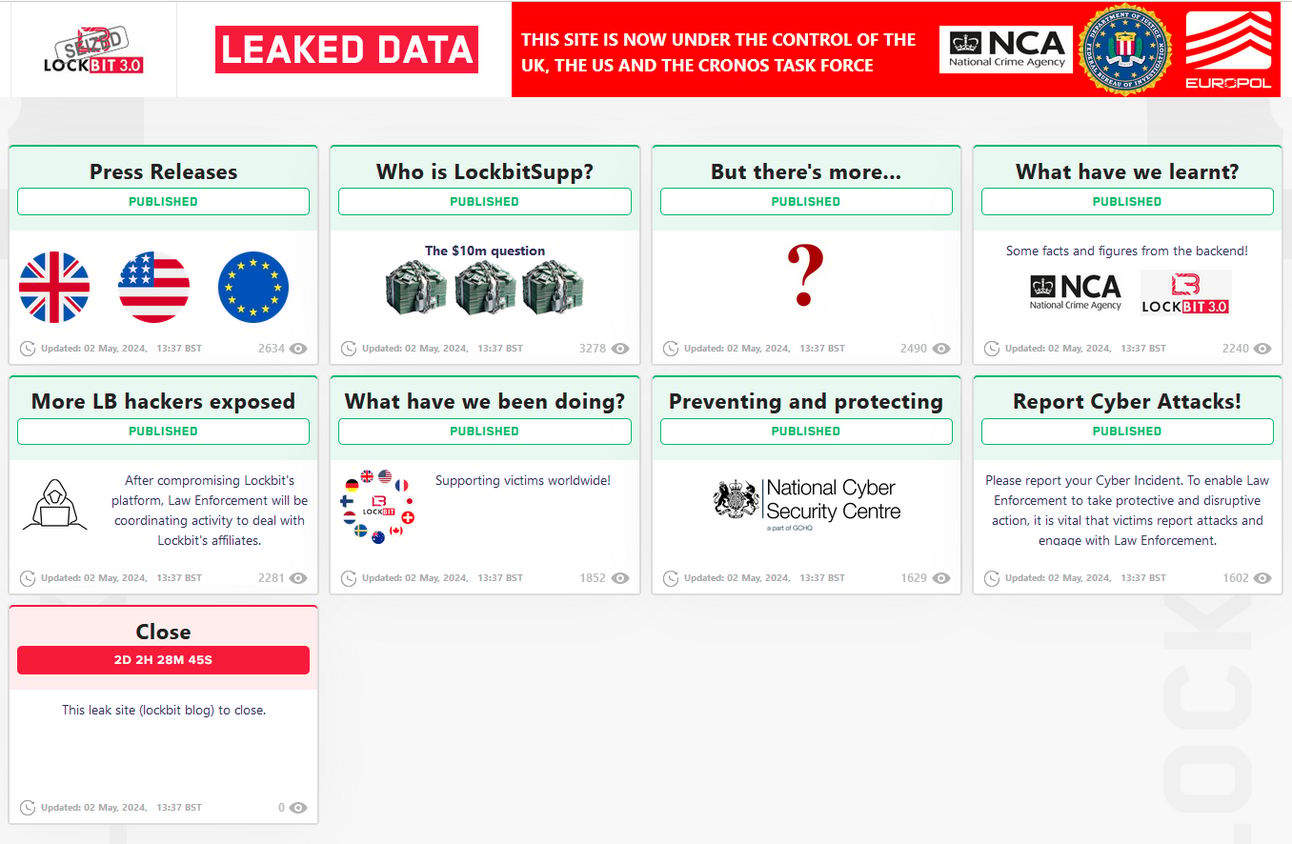
Lockbit’s seized leaksite updated home page
Whereas last time, we were all disappointed because we received almost no information on LockbitSupp's real identity, law enforcement came through this time.
They dropped LockbitSupp's alleged real identity! He is…drum roll, please…a 31-year-old Russian national named Dmitry Khoroshev.
And we learned that he has an iCloud account and that his biceps are the only thing bigger than his ego. It's good to know that you can steal hundreds of millions of dollars from people and still have time to hit the gym.

From Lockbit’s old leaksite
In a statement that is as convincing as your deadbeat friend saying they’ll pay you back, LockbitSupp claims the FBI has the wrong person. While dropping over 70 more victims onto their leaksite, Dimitri also found the time to launch a contest to see who can contact the “real” Dimitri or his relatives to see how he’s doing. Anyone who does, will get $1000 and likely added to the FBI watch list.
The Lockbit saga continues…
News
What Else is Happening?
🤖 Android users in Finland are seeing a wave of text messages asking them to call a service number. Unsuspecting victims are instructed to install malware on their devices, which aims to withdraw money from their online bank accounts.
🪪 80% of El Salvador’s residents had their PII stolen and posted on the dark web. The leak also included name, birthday, phone number, email address, and home address. Interestingly, the leak also included over 5 million high-definition photos, which is considered biometric data. This can be powerful in the age of deepfakes to support identity theft.
🧹 We’re not in Kansas anymore…oh wait, that’s just because the city of Wichita took its online services offline following a ransomware attack. In case you were wondering, the landfill only currently accepts cash payments.
🏥 Healthcare is still in the crosshairs of ransomware. This week’s target is Ascension, a large private healthcare provider with 140 hospitals in 19 states. The cyberattack took the electronic health records systems offline, and out of an abundance of caution, Ascension has paused non-emergent elective procedures, and some ambulance services are being diverted to other hospitals.
🌐 Dell started using old tech to identify employees not meeting their return-to-office requirements. Remote workers need to connect to internal resources using a VPN. Combined with badge swipe data, the VPN connections can indicate where users are working from.
🏠 Dell is also dealing with a data breach after a threat actor claimed to have the full name, address, and order information for 49 million Dell customers. Perhaps the attacker was looking to send Mother’s Day cards to all the deserving moms out there.
📁 Remember MOVEit from last year? We’re still dealing with the fallout from that. The University System of Georgia sent data breach notifications to 800K individuals whose data was exposed in the Clop ransomware group’s zero-day fun run.
🌊 A spam wave originating from Microsoft 365 caused a delay in emails being sent through AT&T. It’s crazy that it’s 2024, and we still can’t deal with spam.
🚧 A new partnership between Stack Overflow, a popular Q&A site for developers, and OpenAI now allows ChatGPT to use its data for learning and responding to users’ questions. This has angered some anti-AI users who have moved to delete their posts or alter the content. And we thought deepfakes were the only problem we had to deal with…
If you enjoyed this, forward it to a fellow cyber nerd.
If you’re that fellow cyber nerd, subscribe here.
See you next week!



