Wow. What a week for cybersecurity. I would never have guessed that we would see the takedown of LockBit, the most prolific ransomware group in terms of numbers AND the most epic troll by the most unexpected contenders…law enforcement.
This newsletter is all about the takedown of LockBit and all the juicy (and not so much) info that law enforcement dumped throughout the week.
Buckle up because we have a lot of info to get through.
-Jason
LockBit Down
Law Enforcement Takes Down LockBit
On Monday, February 19, 2024, law enforcement seized LockBit’s leak site, replacing the main page with a loading screen that highlighted all the global agencies that participated in the takedown.
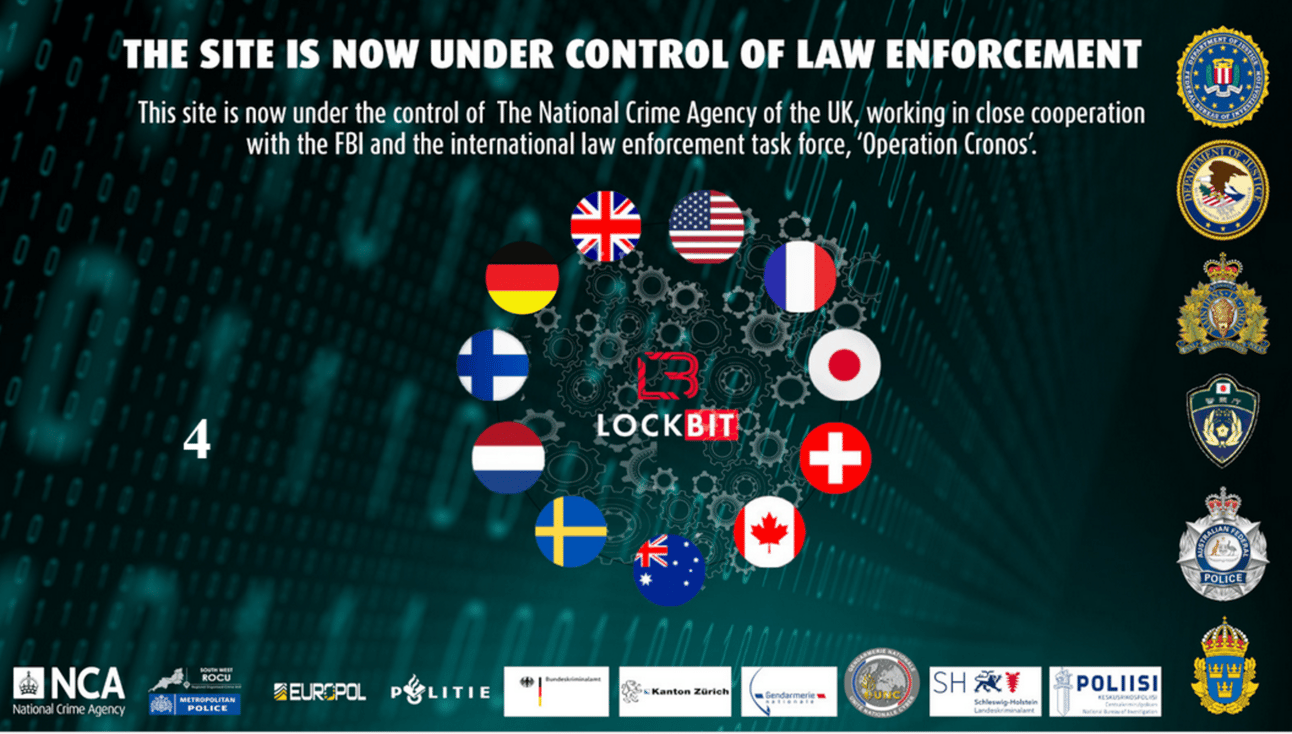
Lockbit Leaksite
After loading, law enforcement’s epic troll against LockBit came into full view. They used the leak site’s blog post functionality, normally reserved for posting stolen information of LockBit’s victims, to post information on LockBit and some humble brags. Don’t worry. We will cover it all in this post as if you were on the leak site yourself.

Lockbit leak Site
Britain’s National Crime Agency’s (NCA) Graeme Biggar announced that his agency had “gained unprecedented and comprehensive access to LockBit’s systems.” But how?
One of LockBit’s leaders said in a thread on XSS, a Russian-language hacking forum, that law enforcement compromised their servers using a PHP vulnerability (CVE-2023-3824) that was disclosed in August 2023. The vulnerability would allow an attacker to execute remote code. What’s interesting with this vulnerability is that an analysis of it showed that it could be difficult to exploit but depends on the application being targeted. I guess a ransomware leak site puts it into the not-so-difficult category.
Exploiting this is difficult to do and heavily depends on the application you're targetting, but possible in theory I think using a combination of stack info leaks and buffer write overflows. People who inspect contents of untrusted phar files could be affected.
While we don’t know for sure how law enforcement gained access, we do know that it succeeded. And they took their time mapping out the infrastructure and gaining total control. They didn’t want to deal with another fiasco like what happened with ALPHV/BlackCat.
To fight against that, the NCA not only went after LockBit’s infrastructure but also…how do we put this in a way that your mom won’t be upset…
They applied blunt force trauma to the groin of LockBit’s operations by attacking the confidence and ego of the group to shake up their ability to rebound while also striking fear into LockBit’s affiliates.
Let’s dig into that now…
Leak Site Deep-Dive
Public Resources for Everyone
While not as much fun for mocking LockBit, law enforcement took the time to ensure all the resources (and bragging rights) were known to the world. This included:
Press Releases: Links to the UK, US, and Europol press releases on the operation.
LockBit Decryption Keys and Recovery Tool:
Information on how to receive encryption support.
Links to a decryption tool created by the Japanese police and Europol.
How to report cyber attacks: A short PSA to report any cyber attacks to law enforcement. While it may seem like law enforcement may not be able to help, in some cases, they can play a pivotal role. In every case, the evidence they collect can help with operations like this.
Make better cyber choices: Instead of Michael Jordan telling cyber criminals to get help, the UK has a national program to help educate people on the difference between legal and illegal cyber activities. The aim here is to help
young, impressionable teenspeople make better choices and stay away from cybercrime.Technical Writeups: Security vendors Trend Micro, Secureworks, and Prodaft supported law enforcement efforts and earned a special place on the leak site…but thankfully not because they were pwned, because they helped to pwn LockBit.
Prodaft: Details on LockBit’s tradecraft
Trend Micro: Details of a new encryptor that was in development
SecureWorks: Details on LockBit’s tradecraft
Leak Site Deep-Dive
LockBit’s Backend Infrastructure
Backend Leaks: The NCA put on their best LockBit impersonation and used LockBit’s leak site to host 12 screenshots of their admin panel, blog post configurations, and core infrastructure configs. Enjoy a smattering of these screenshots for your viewing pleasure.

Stats on leak site activity

Ransom negotiation chats

Production database configuration file

Shadow file for core server (this stores info on users and hashed passwords)
Leak Site Deep-Dive
The NCA Trolls LockBit
The NCA did not waste an opportunity to troll LockBit…and troll them hard. You see, LockBit had been running into some trouble in February 2024 when they didn’t pay an initial access broker (someone who hacks into a company and sells access). Because they didn’t play nice in the sandbox, moderators from these hacking forums banned the LockBit operator account.
Naturally, the NCA was aware of this and decided to do a dedicated troll post showing that they have also been banned from their infrastructure. Well played, NCA…well played.
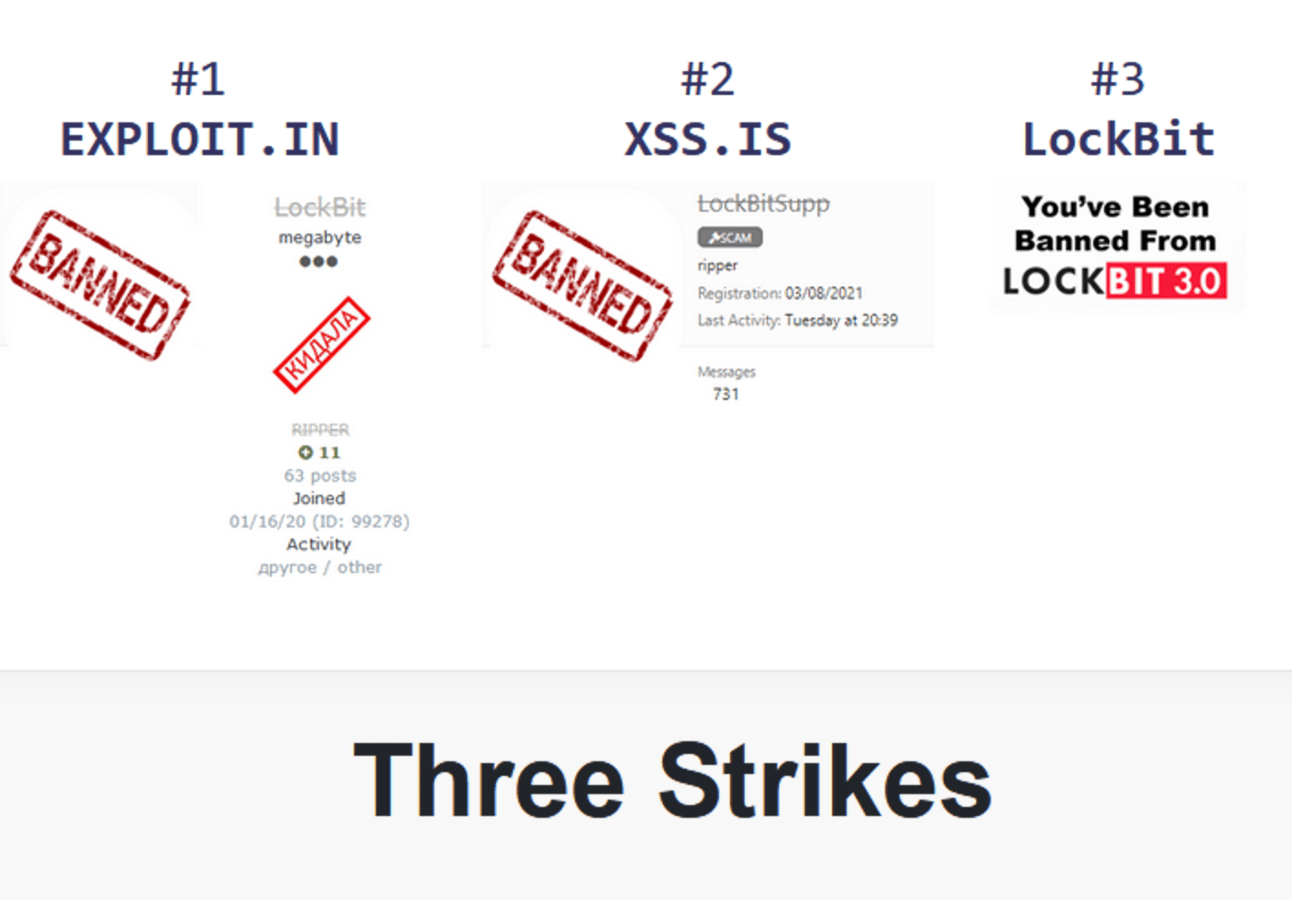
From Lockbit’s leak site
Leak Site Deep-Dive
Arrests, Indictments, and Sanctions

Gif by nounish on Giphy
Good ol’ fashioned police work comes with arrests. And law enforcement didn’t disappoint here.
Arrests: Authorities in Ukraine arrested a father-son duo who were allegedly LockBit affiliates. The same day, authorities in Poland arrested a 38-year-old man in Warsaw who was also tied to Lockbit.
Indictments: The US Justice Department unsealed indictments charging two Russian nationals, Artur Sungatov and Ivan Kondratyev (aka Bassterlord), with using LockBit ransomware in attacks against corporations.
OFAC Sanctions: If you intended to send money to the individuals listed in the US indictment for a meal you shared but kept forgetting to send it, good news. You’re off the hook. OFAC sanctioned them and made it illegal to send them payments.
Leak Site Deep-Dive
Affiliate Infrastructure Goes Bye Bye

Gif by SaregamaPunjabi on Giphy
You must remember that LockBit was a Ransomware as a Service (RaaS) platform that functioned as the tech arm of ransomware operations. They provided the encryptor, the leak site, the negotiation chats, and, in some cases, supported negotiations.
The groups conducting the attacks against organizations were known as affiliates. And LockBit had A LOT of them. According to the screenshot the NCA posted, 194 of them. The fact that law enforcement knows how many should cause affiliates to pause before starting up activities again.

Affiliate list
Law enforcement made sure affiliates knew that. When affiliates logged into the affiliate portal, they were welcomed with the following message.
Hello (user name), Law Enforcement has taken control of Lockbit's paltform and obtained all the information held on there. This information relates to the Lockbit group and you, their affiliate. We have source code, details of the victims you have attacked, the amount of money extorted, the data stolen, cahts and much, much more. You can thank Lockbitsupp and their flawed infrastructure for this situation.....we may be in touch with you very soon.
If you would like to contact us directly, please get in touch.
In the meantime, we would encourage you to visit the Lockbit leaksite.
Have a nice day.
Regards,
The National Crime Agency of the UK, the FBI, Europol, and the Operation Cronos Law Enforcement Task Force.
Leak Site Deep-Dive
Data Theft No More

14,000 Rogue Accounts Closed: In addition to shutting down affiliate infrastructure, law enforcement coordinated the closure of over 14K accounts across Mega, Tutanota, and Protonmail that were used as part of affiliate activities. This included their overall infrastructure, email comms, and hosting stolen data.
StealBit = Donebit: Law enforcement also seized servers used for Stealbit, LockBit’s custom data exfiltration tool that automated data theft from victims’ systems all the way to Lockbit’s blog.
Oh, and if you were wondering whether Lockbit ever deleted files once victims paid…even though they pinky swore…NCA reported that they still had the data.
So in the surprise of the century, we learned that we can’t trust the hackers that broke into your organization, stole your data, encrypted all of your files, were jerks while negotiating a ransom payment, and probably were laughing at you the entire time.
I’m shocked, absolutely shocked. 😲
Leak Site Deep-Dive
LockBit Had Money…Lots of Money

Giphy
While law enforcement froze 200 crypto accounts, they also took time to analyze the information they collected from their access to LockBit’s systems. They tracked and monitored thousands of cryptocurrency addresses linked to LockBit. While their investigation is ongoing, they did report the following stats from just July 2022 to February 2024:
30,000 BTC addresses collected from LockBit’s systems
Over 500 active addresses received over $126 million USD at today’s BTC value.
Over 2,200 BTC are unspent, a whopping $114 million USD at today’s BTC value. This is largely from the 20% fee affiliates pay to LockBit from a ransom payment.
The full infographic posted to the leak site is shown below.
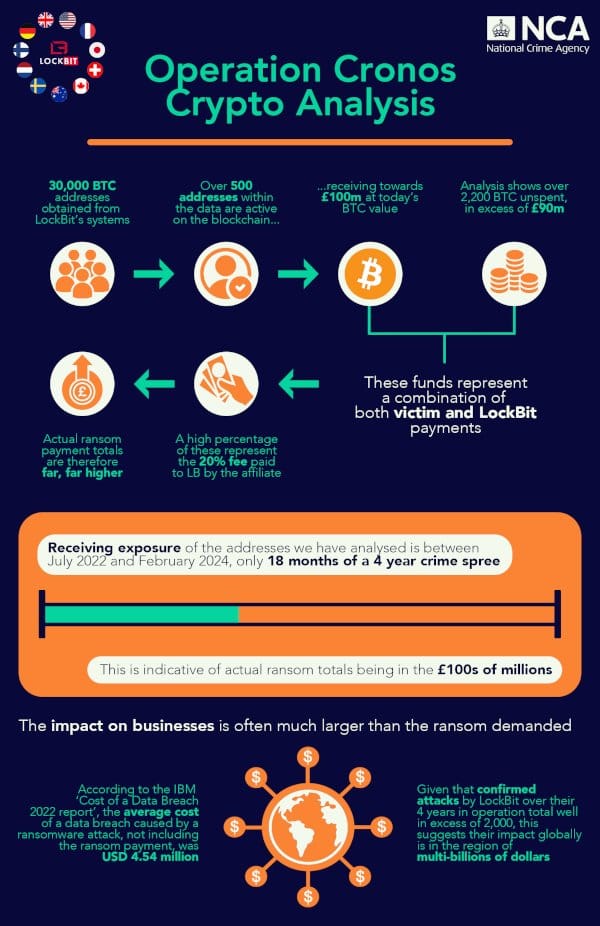
From LockBit leak site
Leak Site Deep-Dive
Law Enforcement Plays Guess Who
The post we had been waiting for all week was to see evidence of who the real identity behind Lockbitsupp was. All the waiting…was not worth it 😭.
All we learned was that the person did not live in the US or the Netherlands. But they did drive a Mercedes…so that’s cool, I guess?
Law enforcement left us with a cliffhanger, claiming they know who he is, where he lives, and how much he is worth.
Oh, and also that he has engaged with law enforcement…
It’s unclear whether this is accurate or just an attempt to build a further divide between LockBit and its affiliates. Either way, it should cause people to pause before jumping back into any reincarnation of LockBit.

From LockBit’s leak site post
So, What’s Next?
Will LockBit Go Down Silently?
As you can tell, law enforcement’s actions were wide, and they caused a lot of damage. Not only to LockBit’s infrastructure but also to their trust and confidence.
vx-underground contacted LockBit’s admins and asked them their thoughts on what’s next.
Their reply?
They’re restoring their infrastructure and will have a formal reply to law enforcement once that’s finished.
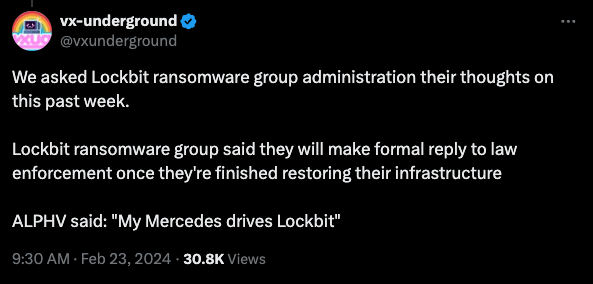
From vx-underground X Post
As for their real identity, vx-underground reported that the persona behind LockBitSupp upped a bounty for anyone that could provide his real identity to $20 million USD.

From vx-underground X Post
I guess we’ll wait and see how this all plays out…
So, What’s Next?
We Have Our Answer
Naturally, just as I finished writing this, LockBit popped up from the shadows. Nearly five days after their systems went down, LockBit is back with a new leak site. Their first listed victim? The FBI…

via vx-underground
They have already started putting prior victims on the leak site, including Fulton County, Georgia.
The LockBit operator was not short on rhetoric either. In a nearly 3K word essay, they discussed what happened. Here are the highlights:
They claim the FBI hacked their servers on February 19, 2024, using a PHP exploit (discussed above), though later admit they weren’t sure how long the FBI had access to the systems. They claim they became lazy after making so much money and didn’t update their PHP version. The odd thing about this is that the FBI would have needed so more time to collect information and plan everything. So LockBit gets an “F” for a terrible investigation.
They also claim that the FBI timed this with the Fulton County, Georgia data leak because they had information related to Donald Trump. It then goes into political propaganda and calls for more attacks against “.gov” targets.
LockBit rebuilt their infrastructure from available backups, which they claim did not have PHP running, and that is why the FBI could not access them. They took additional precautions this time to segment more of the infrastructure so that affiliates each have their own server. Good resilience.
After boasting about how much attention the FBI paid to them and how that means they’re awesome, they offer the “pentester” from the FBI a job with them if they make less than a million dollars. They then make the claim that they think it was someone from Prodaft (listed above).
After a lot of trash talk about the FBI, they then go on to highlight that new affiliates can work with them as long as they have a reputation and can prove they are pentesters.
So, I’ll repeat this again…I guess we’ll wait and see how this all plays out…
News
What Else is Happening?
Wow, did you make it all the way here? This week’s newsletter is a deep dive into a single topic, so we’re skipping the weekly news.
If you want a quick 30-second recap of each week’s cyber happenings, subscribe here to stay in the know.
If you enjoyed this, forward it to a fellow cyber nerd.
If you’re that fellow cyber nerd, subscribe here.
See you next week!







