The best part of owning a home is when your new HVAC system starts throwing a random error code that the techs have no idea what it means and will require multiple visits to address. This is why warranties were made.
Thankfully, in the cyber world, nothing ever goes wrong. Oh wait…today, we’re covering:
Using AI to create exploit code
Key trends from Mandiant’s M-Trends report
Attackers are targeting Japanese trading platforms
-Jason
AI Spotlight
AI Exploit Development

Well…sh*t. Matthew Keely, a security researcher, tested using AI to build working proof of concept (PoC) code for a known software vulnerability…and it worked.
Let’s explore how he did it…and what it means going forward.
It started on Twitter X. Matthew was scrolling and found a post about a new vulnerability in the Erlang/OTP SSH server. The post highlighted the new vulnerability but did not provide a PoC for the exploit. That was not good enough for Matthew. He had a thought.
Could AI write the exploit? Yuuuup. Erlang is open-source software, so to start, Matthew pulled two versions of the code: the vulnerable version and the patched version. This is almost cheating (but encouraged) because you can see exactly what the developers had to fix that was vulnerable before.
Matthew then used ChatGPT to do the following:
Write a Python script to find the differences between the two code versions.
Using the differences, determine what caused the vulnerability.
Write PoC code for the exploit.

Here’s ChatGPT’s output that showed the root cause of the vulnerability.
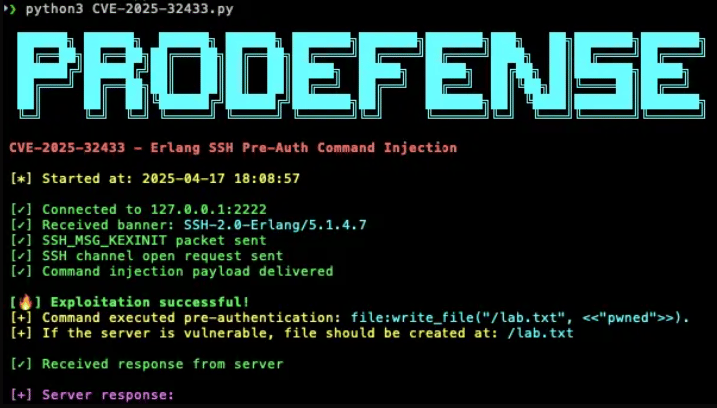
The first iteration of the exploit code didn’t work. No biggie. Matthew switched over to the Cursor AI coding platform and asked it to fix the PoC code. It found all of the issues and got it running faster than Scooby Doo after he says “ruh roh”.

Here’s a view of the final output of running the exploit code. Looks fancy.
This is good and bad. It’s good for defenders because this can and should be automated to test code for vulnerabilities or see how likely an exploit is before it becomes public. It’s bad for defenders because attackers can now automate writing certain exploit code, which was a barrier for some before.
As I mentioned, this scenario was playing the game on easy mode because it was open-source code. But Matthew's steps are standard for security researchers when new exploits are dropped without a working PoC. So it’s a real-world situation.
Product companies must incorporate this level of testing in their code before it goes into production. For a mature application security program, this may already exist in the form of SAST (Static Application Security Testing) and DAST (Dynamic Application Security Testing), which are automated ways of looking at code to find vulnerabilities. Unfortunately, this is something that can often be an afterthought.
Security Deep Dive
The Most Wonderful Time of the Year - Annual Security Reports

Mandiant’s latest M-Trends report is out. They distilled findings and trends from over 450 thousand hours of incident response engagements into a short report that is 92 pages long (my main complaint for most annual reports is that they’re too damn long). This means that only 17 people will read it word for word because nobody has that attention span in 2025.
Because I ❤ you, I pulled the main thing I pay attention to each year. Initial access.
How the f*ck are these attackers getting into companies? Mandiant continued to observe exploits as attackers' top method of gaining access to victim environments. Edge devices, like VPNs and firewalls, continue to be a top target for attackers because, by design, they have to be Internet accessible. Mandiant observed Palo Alto, Ivanti, and Fortinet as the top three targets.
In second place were stolen credentials. The surge of infostealer malware and data leaks are driving this increase. Attackers will jump back and forth between stolen credentials and exploits, primarily driven by the availability of exploits.

With Mandiant, you must account for all the nation-state investigations they do. It skews the perspective. Thankfully, they separated the initial access for ransomware attacks, which tells a different story. In this case, the top two methods of access involve credentials. The top one was brute-forcing weak passwords, followed by our familiar friend stolen credentials.

Let’s not forget cloud breaches. For whatever reason, they don’t get as much attention. Maybe that will change with Google’s $32B acquisition of Wiz. When it comes to the cloud, it’s largely about stealing credentials, whether that be passwords or access keys.
Email phishing was the top infection method there. You can bet there was some MFA bypass with that as well. On that note, SIM swapping popped up in 6% of the infections.
Once attackers gained access, Mandiant found that data theft was the primary objective in 66% of the cloud compromises they identified.

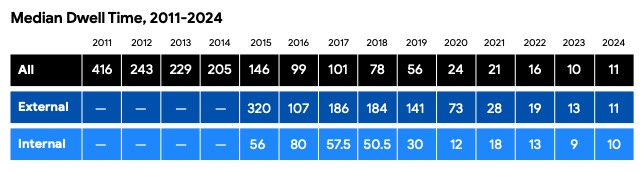
Of course, everyone loves the dwell time stat. In 2024, Mandiant observed an average of 11 days from when attackers gained access to the environment and when they were discovered. That’s much better than the 205 days from 2014. Why the change over the last decade?
For one, ransomware started to tip the scales. No sense in staying quiet when you’re just aiming for mass destruction to get a ransom payment.
But we can also see that companies are doing better at detecting attacks. Interestingly, Managed Detection and Response (MDR) gained a lot of steam in 2016 when Gartner published their first market guide to MDR.
It could be a coincidence, but I see that as a telltale sign that companies started to take detection and response much more seriously. Of course, EDR technology continued to improve over that time as well.

Security & AI News
What Else is Happening?
💳 A fake bank security alert about a rogue payment prompts you to call a number to protect your bank account. Scammers use this to social engineer you into giving up your credit card number. Once they have you on the phone, they’re getting you to give up your PIN, remove card limits, install malware on your cell, and ultimately trick the user into transmitting their credit card information through that malware to buy things somewhere on the other side of the globe.0
🥸 Scammers are impersonating FBI Internet Crime Complaint Center (IC3) employees. IC3 is where you report cyber fraud…oh, the irony. The scammer starts by reaching out via email, social media, or phone calls claiming that they recovered funds from a scam the target was involved in. To get the refund, victims must give up sensitive financial information that the scammers can use to conduct fraud.
💸 Japan is warning of an increase in attackers using stolen credentials to log into trading platforms and steal all the money. They noted that between February 2025 and April 16th, 2025, there were over 3,300 unauthorized accesses, with 1,454 fraudulent transactions netting millions of dollars. The stolen credentials were sourced from phishing sites that impersonated the trading platforms.
🤦 I didn’t think this needed to be said, but please don’t start a newsletter, get lonely, create an AI employee, hit on the AI employee, and then create a blog post about it…it’s just weird.
If you enjoyed this, forward it to a fellow cyber nerd.
If you’re that fellow cyber nerd, subscribe here.
See you next week, nerd!