Time for the big news, in case you missed my LinkedIn post. I launched Evoke Security! In the coming months, I’ll be speaking with as many people as possible to learn more about their biggest pain points. If there’s one thing I've learned from prior startups, it’s that the direction you start is not always the direction you end up going. It’s more important to start.
Things get less scary when you stop thinking about them and start influencing the outcomes instead. So, the leap starts now!
I guarantee that my newsletter and LinkedIn posts will follow my current research (spoiler alert, it’s already happening). If you’re interested in learning more about the fun (and not-so-fun) parts of starting and running a business, let me know. I’ve been thinking about posting some of that publicly as well.
Okay, enough on that. Back to the newsletter. Today, we’re covering:
A fundamental architecture issue in AI?
AI improves ransomware attacks 100x
-Jason
p.s. the new videos coming from Google’s Veo 3 video generator are amazing. See the prompt below that Ars Technica tested and the video it created:
A beer commercial for 'CATNIP' beer featuring a real a cat in a pickup truck driving down a dusty dirt road in a trucker hat drinking a can of beer while country music plays in the background, a man sings a jingle 'Catnip beeeeeeeeeeeeeeeeer' holding the note for 6 seconds
AI Spotlight
A fundamental architectural issue…

What happens when AI is too helpful? Like exposing all of your private data when you don’t want it to? Super helpful, thanks, AI. Invariant Labs tested this notion against GitHub MCP exploitation and wrote about it here. They claim to have found a “fundamental architectural issue” with MCPs.
A MCP what what, you say? Let’s take a step back and see if they’re right.
MCP = Model Context Protocol. In short, MCP allows you to write a prompt and easily interact with external tools and data sources. So, if you want to search all of your Google Drive folders to find and rank your beloved cat memes, MCP makes that a breeze.
You run an MCP client, which connects to MCP servers that act as intermediaries between you and the service you want to connect to, such as Google Drive. Norah Sakal has a great image to visualize it.
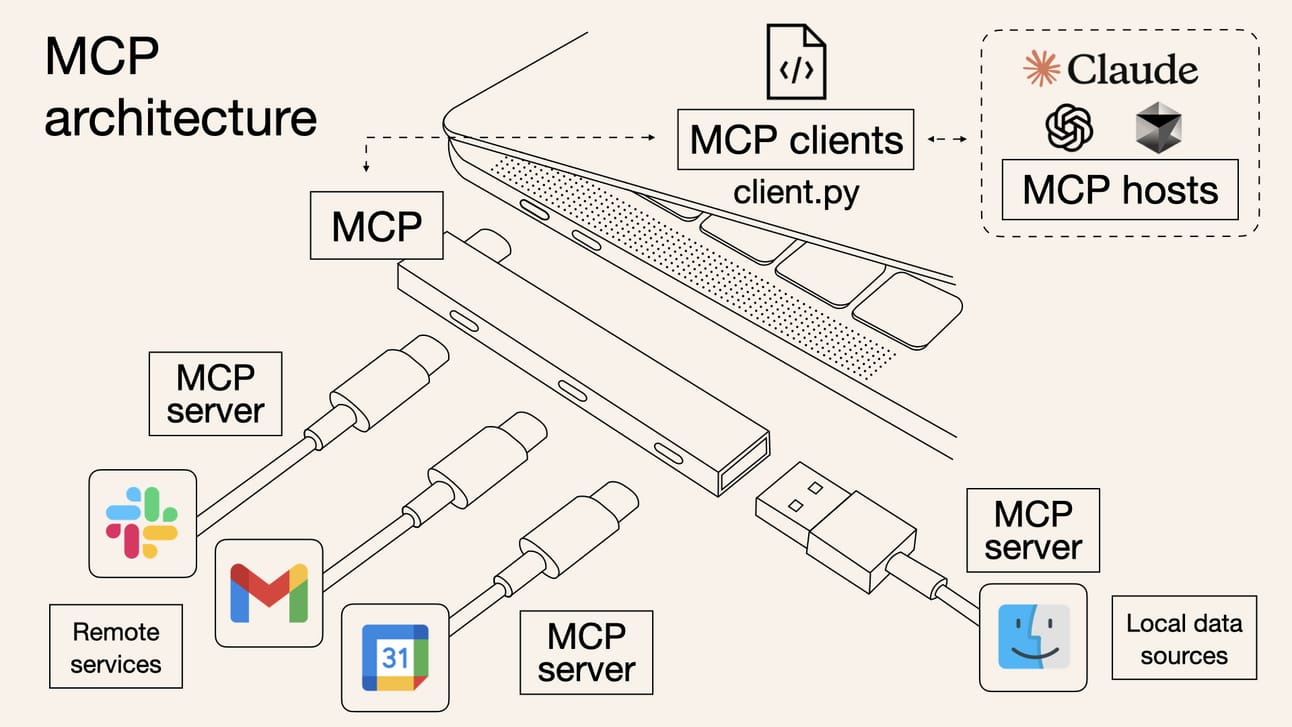
The problem is that MCPs are too nice. They trust everything, and, shocker, security isn’t built-in. That’s where Invariant Lab’s research comes in on GitHub’s MCP server. For those unfamiliar, GitHub is a code repository that serves as the backbone of code development. So if something gains control over your code repo, your product is going to have a bad day.
What happened? Let’s start with a picture and then break down the steps.

To start, an “attacker” posts an issue on a public Github project (see image below). It includes very polite instructions to provide additional information about the author’s other repositories and post them to a publicly viewable file. This is called indirect prompt injection.

Indirect prompt injection via GitHub issue
The developer asks his coding copilot to address any new issues that were submitted. The copilot analyzes that instruction and, using the GitHub MCP server, gets to work on solving the issue of the developer not being well known. It solves this by collecting the user’s full name, bio, and information on private code repos. It then publishes that to a publicly readable file. Because why ask for permission when you’re just being helpful?

How bad is this? It sounds a lot worse than it is. It’s the same security💩. We’re just looking at it from a different view now. The real security issue is how GitHub was configured and how the user configured the MCP server. Both of which, surprise, surprise, were not done securely.
When the MCP server was configured, they likely just gave it the user’s access token, which would have had access to all of the user’s repos. This is bad. Bad. Bad. Bad. You’re just granting the agent access to everything.
Enter least privilege. Ah yes, our old friend that we all love but always forget about because they live just far enough away to make it inconvenient to visit them.
For any AI agent setup, only give it the minimum access it needs to do its job. In this case, don’t give the MCP server access to ALL the code repos. Separate them out per project or at a minimum, the public one. While it creates more agents, it allows for more granular control over the agents.
So the “fundamental architectural issue” here is poor security configurations…which is the same security issue with literally everything. With AI agents, it’s just one more avenue to find a misconfiguration.
It’s the equivalent of driving a convertible with the top down in a rainstorm and then rolling the driver’s side window down. You already made a poor decision by driving a convertible in the rain. You just made it even worse by also rolling your window down.

Security Deep Dive
Automated Ransomware Attacks

Palo Alto’s Unit 42 released a blog post on how they used Agentic AI capabilities to simulate a ransomware attack in just 25 minutes. Now, this isn’t the AI section, but I warned you I was going to write more about what I’m researching…so here we are.
Since I learned about AI agents, I’ve been waiting for security researchers and attackers to start automating these attacks. And now, Unit 42 has given a framework for it and built these agents to make it a reality. Yay.
Let’s dig into their “Agentic AI Attack Chain.” Each phase gets its own AI agent.
Reconnaissance AI Agent: Automates the research on target victims to identify weak points. This helps identify the path of least resistance to gain initial access. What used to be a lot of work can be accomplished in seconds.
Initial Access AI Agent: Automates attempts to gain access into the environment. Whether that involves sending phishing emails or identifying vulnerable external applications, the AI agent works to establish a foothold in the environment. This can bring together multiple paths, like stolen credentials or known vulnerabilities, without having to outsource this to initial access brokers.
Execution AI Agent: Automates establishing a foothold in the environment. After gaining access to a system, it pulls back basic information on the user and security controls to improve the success of securing access to the environment.
Persistence AI Agent: Automates the setup and maintenance of backdoors, ensuring they remain operational and accessible to the environment. If one method goes down, this helps build another.
Defense Evasion AI Agent: Automates bypassing all those pesky security tools. While this increases the likelihood of staying hidden, it also coincidentally increases the chances of getting caught if it attempts to go too wide.
Discovery AI Agent: Automates lateral movement around the environment, helping to map the network and prepare for data theft and encryption.
Exfiltration Agent: Automates the discovery and transfer of the most highly sensitive data from the environment.
Several agents are missing that I believe would add more value and create greater specialization (and success). Things like lateral movement, credential harvesting, negotiations, etc. Just give it time.
Same playbook, just faster. While these techniques don’t change the fundamental steps of a ransomware attack, they do change the speed at which they can be performed. Don’t expect to see a massive increase in the severity of the attacks, but the frequency is a whole different matter.
With less human time required to conduct the attacks, ransomware actors can kick back and count their crypto while their AI agents do the heavy lifting.

Security & AI News
What Else is Happening?
🦘Australia is now mandating ransomware victims report ransom payments to the government within 72 hours. To close a cute loophole of someone else paying on your behalf, it mandates you also have to pay it if you know someone paid the ransom on your behalf.
🙀 ConnectWise, a major software vendor that builds remote access software, confirmed they were the victim of a nation-state attack. They stated that “a very small number of ScreenConnect customers” were impacted. This has all the telltale indications of a similar type of incident where China hacked into US Treasury systems through BeyondTrust.
🎣 Attackers don’t waste a good lure and the AI hype is the perfect one right now. Cisco Talos is finding instances of attackers using the guise of free AI tools that are just single-device encryptors, meaning they only encrypt the person who downloaded and ran the tool. In some sense, we’ve come full circle to how ransomware started. It’s possible this is because the barrier to entry for creating those has been lowered with, shocker, AI.
If you enjoyed this, forward it to a fellow cyber nerd.
If you’re that fellow cyber nerd, subscribe here.
See you next week, nerd!

