Hey there,
Welcome to this week’s newsletter. Today we’re covering :
Hacker vigilantes sticking it to ransomware groups
How much people are willing to pay for a zero-day
Okta hacked…how bad is it this time?
-Jason
Vigilante Justice - Cyber Style
I don’t often cheer for attackers, but I make an exception from time to time.
The Ukrainian Cyber Alliance (“UCA”) had enough of the Russian-based Trigona ransomware group and took matters into their own hands. They hacked into Trigona’s infrastructure using a critical vulnerability in Confluence’s software.
Ironically, CISA and the FBI warned organizations of this vulnerability on October 16th. Now we know that the Trigona ransomware group isn’t monitoring CISA’s advisories on known exploited vulnerabilities…tisk tisk.
UCA first mapped the infrastructure and then stole data from the developer environment. This included source code, database records, and some cryptocurrency hot wallets.
To add salt to the wound, UCA deleted all of their data and websites. They left a parting gift of a defaced website with the parting message (which I love):
“Welcome to the world you created for others”
Ahhh vigilante justice.
Additional reading:

Zero-Day Vulns are Good Business
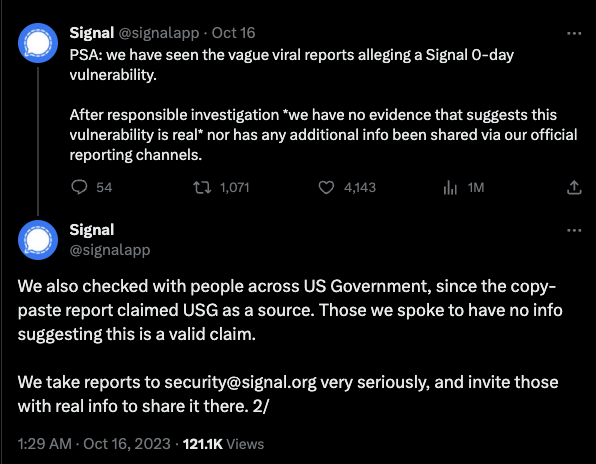
Cyber nerds held their breath for a hot second last week when rumors of a zero-day vulnerability in the popular messaging app Signal emerged. For context, there are over 40 million users of Signal, so this could have been bad.
Signal quickly jumped on this and determined that there was no vulnerability. But that’s not the story here…
The real story is about how much people are willing to pay for a Signal vulnerability.
Settle in class, we’re going exploit hunting.
The Rise of Zero-Days
A zero-day vulnerability is a vulnerability in which no patch exists. This gives attackers a leg up because they can operate unhindered. At least until the vulnerability is discovered and a patch is made available. It’s an attacker’s greatest weapon and is used sparingly due to the cost (time and resources) to identify them.
The number of known zero-day vulnerabilities has spiked in recent years and is likely to increase as more security researchers and governments invest more in finding new vulnerabilities.
Zero-day Brokers
Of course, the difficulty level of finding these vulnerabilities is high, and those skills are scattered worldwide. To fill that skill gap, zero-day brokers entered the market.
A zero-day broker connects buyers and sellers of zero-days. It is no surprise that governments are big buyers of zero-day exploits. They use this as part of their cyber operations for espionage.
You can understand that secrecy between buyer and seller is essential here. The broker helps to not only make the connection but also to serve as a buffer between the parties to help maintain privacy.
Types of Zero-Day Vulnerabilities
The price someone is willing to pay for a zero-day is related to a few key factors, including:
The target operating system / application (e.g. Windows vs Mac, Android vs iPhone, or Signal vs WhatsApp)
The type of vulnerability
The type of vulnerability will vary based on mobile or desktop, but generally they include:
Zero clicks: For mobile devices, this involves the user not having to click on anything for execution. For example, this would include a text message auto-generating a link preview and compromising the device without the user clicking on the link.
Remote Code Execution (RCE): The ability to execute commands or malicious code over the network. For example, the infamous ProxyShell vulnerability targeted Microsoft Exchange servers. Attackers could remotely scan the Internet and execute code on vulnerable servers.
Local Privilege Escalation( LCE): The ability to run commands or code as a higher privileged user. For example, a standard user on a desktop could run code as an administrator.
Full Chain with Persistence (FCP): For certain devices and applications, multiple vulnerabilities must be chained together to bypass security features. This adds complexity and difficulty where a chain of vulnerabilities must be found to execute code that can run again on the next system reboot (persistence).
The Cost of a Zero-Day
So, how much are some people willing to pay for a zero-day? Spoiler alert…a large amount of money.

Gif by DominaSeries on Giphy
Some zero-day brokers will pay upwards of $2.5 million USD for an Android full chain zero click vulnerability. Here’s a sampling:
Android Full Chain Zero Click: $2,500,000
IOS FUll Chain Zero Click: $2,000,000
Signal RCE: $1,500,000
Whats App RCE Zero Click: $1,500,000
Chrome RCE: $500,000
Windows LPE: $150,000
Apache / MS IIS RCE: $500,000
So you can see, in the instance of Signal (where we first got on this tangent), buyers are willing to shell out $1.5M USD. That could be a small investment if you have a market size of $40 million people. That’s a good sample size for your mission, whether espionage or financial gain.
Additional Reading

Okta Breach…How’s it Looking?
It wouldn’t be a Friday in cyber security without some major breaking news. This time, it was the well-known Identity Provider Okta. They provide Single Sign-On (SSO) and MFA services for many organizations.
Details are limited so far, but here’s a quick recap of what we do know:
An attacker gained access to Okta’s support management system. Based on Okta’s blog post, it appears the attacker used stolen credentials to gain access.
It’s unclear how the attacker obtained valid credentials or whether MFA was enabled on the account. Social engineering is a straightforward way to deal with both.
The support management system is separate from their production environment and is used to troubleshoot customer issues.
The attacker used this access to search for customer tickets and the data shared with Okta.
Customers commonly share HTTP Archive (HAR) files with Okta for troubleshooting. This is essentially a recording of a web session. It includes everything involved with a browsing session, including session cookies - a common target for attackers.
Check out my TeachMeCyber video that shows how attackers steal session cookies in phishing attacks.
The attacker found HAR files of juicy targets, extracted the session cookies, and used those to access Okta’s customer’s Okta accounts.
So, the question remains: what’s the impact of this?
It appears the attacker had access to the support management system for at least two weeks. That is enough time to dig into many support tickets and get a lot of HAR files to search for session tokens.
We know of two organizations impacted so far, Cloudflare and BeyondTrust.
My initial reaction is that the impact will be fairly limited, at least in the number of impacted customers. Where this could expand is the compounding impact of which Okta customers were affected and what the attacker could do with that access.
Cloudflare and BeyondTrust detected and stopped the attacks before damage could be done, though I imagine other impacted organizations are still investigating.
Many variables dictate the possible number of impacted organizations, including:
The number of organizations that uploaded HAR files and how long that data was retained.
The session timeout on session cookies. This is configurable by the organization, so it could vary widely.
This is a reminder for every organization to force strong MFA and limit session times as low as possible.
I’ll continue to keep an eye on this. If it escalates, we’ll chat more about this next week.
Additional Reading
Feedback, questions, or topics for future newsletters? Please reply to this email directly and let me know.
Get these weekly insights delivered to your inbox.
Share this with a friend! It helps me grow the newsletter.
See you next week!