Good morning. For those following along, I lived to fight another day without a snow shovel. The victory was short-enjoyed, though, as more Internet outrage occurred after another security incident, this time with the SEC’s X account (more on this below).
I’m starting to wonder if the Internet’s voice ever gets hoarse from shouting so much…
Anyway, today, we’re covering:
A new twist on ransomware extortion
The blame game double standard?
New year, new social engineering tactics
-Jason
Spotlight
New Ways to Swindle Ransomware Victims

Ransomware attacks are one of the most violating cyber attacks. Not only do the victims have to contend with the fact that their cyber defenses failed, but they also are forced to deal with their systems being down and legitimate threats of their data being released to the world.
This is an evolution of 10+ years in the making with ransomware attacks. It started from single-system encryption to the current state of pure chaos. Ransomware victims no longer have the luxury of hiding, even from other attackers.
Attackers always refine their approach to maximize profit. We see instances where they extort their victims a second time. While rare, sometimes the initial ransom payment is not enough. They demand more money before they delete data or give you a decryption key. In other instances, stolen data was supposed to be deleted after receiving the ransom payment, and then...Surprise, it’s not deleted! Now another attacker has the same data and is extorting you again.
Just when you thought it couldn’t get any worse. A recent Arctic Wolf blog post shed light on a new extortion tactic that is just mean.
The security company saw two instances where an attacker contacted a ransomware victim with a “deal.” In one instance, the attacker claimed to have gained access to the backend infrastructure of the ransomware group that originally encrypted the victim’s systems. In another, the attacker offered to hack into the ransomware group’s servers.
In both scenarios, the “friendly” attacker asks for payment to access the ransomware group’s servers and delete the victim’s data.
One thing is certain. It’s easy for any attacker to make claims of capabilities or actions they’ve taken. The burden of proof is largely on the victim to quickly see if they were hacked or not to figure out if the claim is valid. Or if the data even originated from their systems vs a third party.
It should go without saying with these new techniques, just don’t. If you even have an inclination that it might be a good idea, just stop.
Deep Dive
The Outrage Double Standard

On Tuesday, January 9th, 2024, some interesting things happened on X. The SEC’s X account posted about approval for Bitcoin ETF listings, and the Internet rejoiced…one problem, though. It wasn’t true, even though it looked legit, as shown below.

Fake Bitcoin ETF post via the compromised SEC account. Via Yahoo Finance
An unknown attacker hacked the SEC’s X account and made that post. The attacker even got some practice in before hand. They posted a less sophisticated post, shown below, before quickly deleting it and opting for a more professional look. Because, you know, even attackers have design standards.
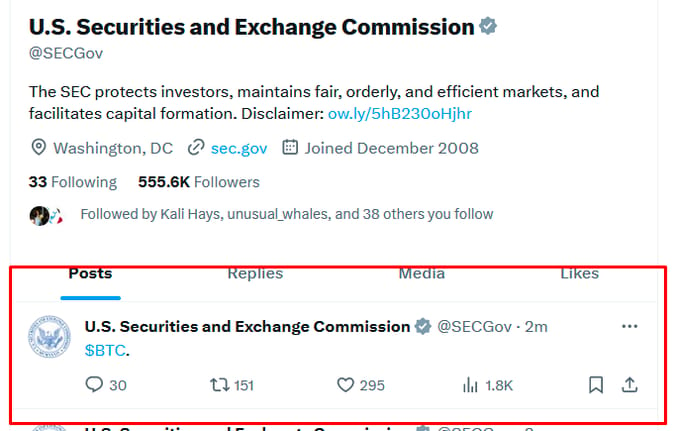
Via FatManTerra
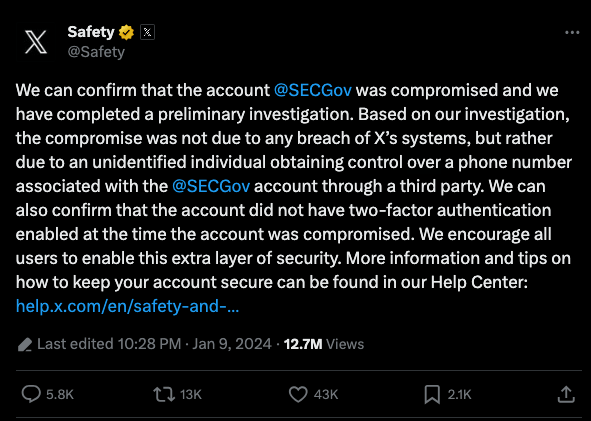
What made this even more confusing is that the SEC was required to issue a decision on the Bitcoin ETFs by the next day, Wednesday January 10th. So this type of announcement was expected, causing some to think someone botched the scheduling of the post instead of the account being hacked. Though the SEC confirmed the account was compromised in a later post, shown below.
While that was pure chaos, what happened next just added salt to the wound.
It’s not a secret that Elon Musk and the SEC aren’t BFFs. But you would still expect some level of respect for the situation. Instead, the X Saftey team posted that X wasn’t hacked as some began speculating. Instead of stopping there, the X Safety team offered up additional detail on the the attack and aggressively pointed the finger at the SEC, as you can see in the post shown below.
In an interesting move, they included details on what happened to the SEC’s account. Piecing together the details and how these attacks usually go down, here’s the likely scenario:
An attacker conducted a SIM swap attack to obtain control over a phone number associated with the @SECGov X account.
The attacker then conducted a password reset using the phone number they now controlled.
The attacker then logged into the X account with the fresh password.
From there, the attacker would have full control of the X account. They used this access to issue the above posts and “like” different crypto posts.
Note that the SEC did not have MFA configured on the account, which may have prevented the attacker from logging in.
In cyber security attacks, the masses love to point the finger at someone. Last week, the Internet lost its mind after 23andMe “blamed” users for reusing passwords and not enabling MFA on their accounts, which they claim led to the account takeover of nearly 14K accounts.
The Internet was upset because they called out that it should be 23andMe’s responsibility to secure their users’ accounts from such attacks. Including mandating MFA on attacks and protecting against users who reuse passwords.
Flash forward to this week, and you have X’s Saftey team publicly commenting on the security controls of one of their user’s accounts (am I the only one that thinks that’s odd). Unsurprisingly, they called them out for not having MFA enabled. The Internet then began a crusade against the SEC for not taking the precautions of putting MFA on their account.
It’s not an apples-to-apples comparison, sure. But that doesn’t mean we can’t learn something from this. In both cases, we rush to point fingers instead of identifying the true security gaps that contributed to the attacks (spoiler alert, everybody plays a part in contributing). And somehow, we always forget to blame the attacker as the primary culprit here. Funny how that works…
While it may make us feel better to hold someone accountable, it doesn’t fix anything.
Instead, let’s focus on the outcome we are looking to achieve. In all of these hacks, we can see a clear need to enforce MFA for users. For too long, companies have feared that enforcing MFA will cause user retention issues, hurting their long-term profits and valuations.
Then we look at Microsoft. They released a blog post last year that destroyed this idea. After mandating MFA for their consumer accounts (e.g. Outlook.com, Skype, Xbox, and OneDrive), they saw the following results:
100% adoption of MFA within 60 days (accounts are blocked at 60 days until they set up MFA)
Reduced account takeovers by 80%
Fake account creation reduced by 99%
Self-account password recovery increased to over 90%
Customer retention increased 5%
It’s time for everyone to step up. Companies must lean into the mindset of “secure by default.” They must guide consumers to the right security settings that will help prevent account takeovers. And for consumers, you’re not off the hook either. Everyone must get smarter on their password practices and use a password manager and MFA. It won’t be perfect, but we all can do better.
We need less rhetoric and more understanding.
We need less blame and shame and more shared learning.
We need less outrage and more action.
News
What Else is Happening?
💰 New year, new phishing emails. The email security company, Cofense found that attackers are using annual employee tasks to steal credentials. Specifically, they’re sending phishing emails about open enrollment, 401k updates, salary adjustments, and employee satisfaction surveys (I hope they save the results).
🇺🇦 BlackJack, a pro-Ukraine hacking group, claims to have revenge hacked the major Russian telecom provider, M9com. The group said they stole data before wiping 20 TBs of data. This was in retaliation to the Russian attack against Kyivstar late last year.
🐘 The Toronto Zoo was the victim of a ransomware attack. We’ll call out the elephant in the room and tell you that no animals were harmed due to the attack.
⬇ Stop downloading free software from links in YouTube video descriptions. Fortinet’s research team found attackers are using YouTube channels featuring cracked applications to distribute infostealer malware.
If you enjoyed this, forward it to a fellow cyber nerd.
If you’re that fellow cyber nerd, subscribe here.
See you next week!