Hey there,
In this week’s newsletter, we’re covering:
ChatGPT goes down during an AnonymousSudan DDoS bender
Cl0P drops another zero-day
-Jason

AnonymousSudan Goes on a DDoS Bender
This week, AnonymousSudan claimed responsibility for a DDoS attack that caused intermittent outages for Open-AI’s ChatGPT. While the ChatGPT outages stole the headlines, the hacking group was busy all week tormenting other victims. Here’s a quick timeline:
November 3rd: Yahoo
November 5th: Target
November 7th: Israel Hayorn, El Al Israel Airlines
November 8th: OpenAI
November 9th: Cloudflare
The group uses Telegram to humblebrag about their DDoS attacks. They weren’t shy about saying why they targeted ChatGPT.

From Anonymous Sudan’s Telegram Channel
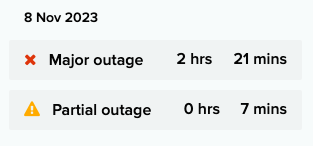
ChatGPT Outage
ChatGPT struggled for a few hours on November 8th but was able to filter out the bad traffic caused from the DDoS attack and restore services.
AnonymousSudan, Who Dat?
AnonymousSudan is a hacktivist group that popped up in January 2023. They claim to be motivated by religious and political causes. While they aren’t shy about posting their reason for launching DDoS attacks, some security experts believe they are tied to Russia. This is largely due to them not attacking Russian targets (even if certain targets would fall in their target profile).
Their Attack of Choice
AnonymousSudan’s go-to attack is the not-so-sophisticated Distributed Denial of Service (DDoS) attack. DDoS attacks flood a target network with a lot of network traffic. It’s said that the amount of volume is equivalent to the noise level of a children’s birthday party, a non-scientific measurement.
This overloads the target’s systems until they can no longer keep up with legitimate traffic. To the outside observer, the web pages appear to be offline.
This video explains how DDoS attacks work.
The group is not shy about touting how they conduct these attacks. Rather than use their own DDoS capabilities, they purchase them through a DDoS service provider.
Their go to way of conducting DDoS attacks? A DDoS as a service platform called SkyNet. For a modest fee of $100 a day or $1700 for one month, anyone can rent the power of a DDoS attack.

From Anonymous Sudan’s Telegram Channel
Because no one would ever abuse that power. How fun.

Additional reading
OpenAI Incident Report

Cl0P Drops Zero-Day in SysAid Software
Background
Microsoft’s Threat Intelligence team dropped a bomb this week. The Cl0P ransomware group (aka Lace Tempest in MSFT parlance) exploited a zero-day vulnerability in the SysAid software.

SysAid is IT service automation software used by IT teams for help desk ticketing and various automation to support IT functions.
Timeline of Activity
The following is the current known activity timeline related to the SysAid zero-day vulnerability.
October 30th
The earliest currently known exploitation of the SysAid zero-day vulnerability (per Joe Desimone at Elastic Search and Huntress ).
November 2nd
The SysAid security team became aware of a vulnerability in the on-premise software. It’s unknown how they were made aware of this.
November 8th
- Microsoft posted on X about Cl0p / Lace Tempest’s use of the SysAid zero-day vulnerability in the wild.
- SysAid posts a blog with details on the SysAid on-premise vulnerability (CVE-2023-47246)
- Profero, an IR firm SysAid hired to support the forensic investigation, posts a blog post with details of post-exploitation activity.
Attack Path
The zero-day vulnerability allows for the upload of a Web Application Archive (WAR) file to the system. The WAR file contains a web shell that allows Cl0P to interact with the system remotely.
Using the web shell, Cl0P then uploads and executes a PowerShell script to download and run GraceWire malware on the compromised system. GraceWire malware is a backdoor that can remotely access and interact with the system. This would provide secondary access to the system if Cl0P loses access to the web shell.
Cl0P then uploads and runs a second PowerShell script focused on anti-forensics. The script deletes the files created during the attack (including the WAR file and GraceWire malware loader). It also deletes specific lines in log files that can be tied back to Cl0P’s activity.
For good measure and added persistence, Cl0P then runs another PowerShell script to download and execute CobaltStrike to the system. CobaltStrike is a post-exploitation toolkit that would allow for lateral movement and ultimately set up the group for a future ransomware attack on the victim organization.
The Impact
The total number of vulnerable on-premise servers appears small, possibly around 418 per a Shodan search. But this doesn’t eliminate the overall significance.

Cl0P has a trend of finding zero-day vulnerabilities and exploiting them at scale before organizations can patch them. This gives them a head start in prepping extortion attacks.
This year alone, we saw Cl0P find vulnerabilities in the GoAnywhere MFT and MOVEit file transfer tools. What followed was data theft and extortion attempts to the victims.
This vulnerability is different from the previous ones. While the previous vulnerabilities allowed for easier data theft, the SysAid vulnerability serves as initial access into an environment. This sets Cl0P up to execute a ransomware attack on possibly hundreds of organizations.
We will have to wait and see how many ransomware victims appear on Cl0P’s leak site in the coming days and weeks.

Feedback, questions, or topics for future newsletters? Please reply to this email directly and let me know.
Not subscribed? Click here:
Share this with a friend!