Here’s a “good feels” hacker story for you. A pair of super nerds security researchers helped some poor dude crack his 11-year-old password that secured 43.6 BTC. Eleven years ago, that was worth $5,300. Today, it’s worth almost $3 million. The next round is on him 🍻
Today we’re covering:
How to predict the future of AI-assisted attacks 🔮
Some major data dumps ❄
Malware that can infect 60% of ATMs 😱
-Jason
AI Spotlight
Red Teaming + AI = ❤❤❤

Gif by PermissionIO on Giphy
To predict how cybercriminals will use AI in cyber attacks, look at the tools red teamers and security researchers create. Companies hire red teams, a team of ethical hackers, to emulate real attacks against their environment. It’s the ultimate stress test for a company’s security posture.
As part of these engagements, good red teams will create new tools or adopt tools that security researchers create in creative ways. It’s no coincidence that mimikatz, one of the most widely used programs attackers use to collect passwords and secrets from systems, was created by a security researcher.
The first line of the readme for mimikatz says:
mimikatz is a tool I've made to learn C and make somes experiments with Windows security.
I guess we’ll just disregard all of the pain caused in the name of “somes experiments with Windows security.”
It’s no surprise that red teamers are experimenting with AI but it’s still early days on refined capabilities. I remember reading this article last year, in which IBM’s X-Force team said they were using GenAI to help with phishing emails. I laughed at it because they stated that creating a phishing email took around 16 hours, and with GenAI, they did it in a few hours. I know last year's inflation was insane, but 16 hours to create a phishing email seems ridiculous. Anyway…
Fast-forward to today, and IBM’s X-Force has more to say about GenAI and hacking. At the recent RSA conference, they talked about how they’re using AI to supercharge their red team engagements.
A key win is in solving big data analysis problems. This is where GenAI, specifically LLMs, excel at. Chris Thompson, global head of X-Force Red said the following:
Technology's finally caught up to where we need it to be to solve these really big data analysis problems, because that's really what red teaming is. You have all the data in the world, you have to collect it really quietly, but then you have to go through lines and lines of code and connect the dots.
Chris said something that I think is the crux of how innovation will compound and deliver the future of AI-assisted cyber attacks.
Now that we have more tools for this offensive data analysis problem, it's just accelerating our work so we can free up our really smart people to solve more interesting challenges instead of just doing that crazy data analysis
When you free up really smart people’s time from mundane and repetitive tasks, you allow them to spend more time solving complex problems. This quickly compounds to bring more advancements in new hacking techniques and tools. If we follow the mimikatz example, cybercriminals will draft off that progress and incorporate it into their own attacks.
My bet on the biggest impact to cybersecurity is on AI Agents. An AI agent perceives its environment and collects data to make decisions. It operates autonomously to achieve specific goals and can improve its performance by acquiring more data and feedback.
Take the specific actions of a hack. Finding an initial exploit, scanning the Internet for that vulnerability, gaining access, escalating privileges, moving around the environment, deploying ransomware, etc. AI agents can be trained in each task, becoming experts in each step. Add in another agent, the orchestrator, who connects the dots between the agents and stays focused on the overarching goal.
While this sounds terrifying, the current advantage goes to the defender. While many of these attack techniques are possible, they haven’t shown up yet in the wild. And defenders have a head start. They’ve used AI for years to detect malware and protect their environments. As red teamers build new tools, security companies improve their detection and response capabilities.
We can imagine a world where every step or function a defender takes to defend their environment can be done by an AI agent. So, while the threat seems scary, we must remember that security has always been and always will be a cat-and-mouse game. Only now we have AI cats and AI mice that are playing the game with us.
Deep Dive
Huge Snowflake Data Plops

Okay, strap yourself in. We have a story to tell on major data dumps and how we got here. As with most things cyber, it’s never a straight route.
A few weeks ago, I wrote about law enforcement taking down BreachForums. Like a villain shaking their fist in the air, ShinyHunters, one of the site's admins, wanted revenge. They regained control of the domain and reopened with something much bigger than a wacky inflatable dude.
One of their first posts was a 1.3 terabyte data dump with info on 560 million Ticketmaster customers. The stolen data, posted on May 28th, includes names, addresses, credit card numbers, phone numbers, and payment details.
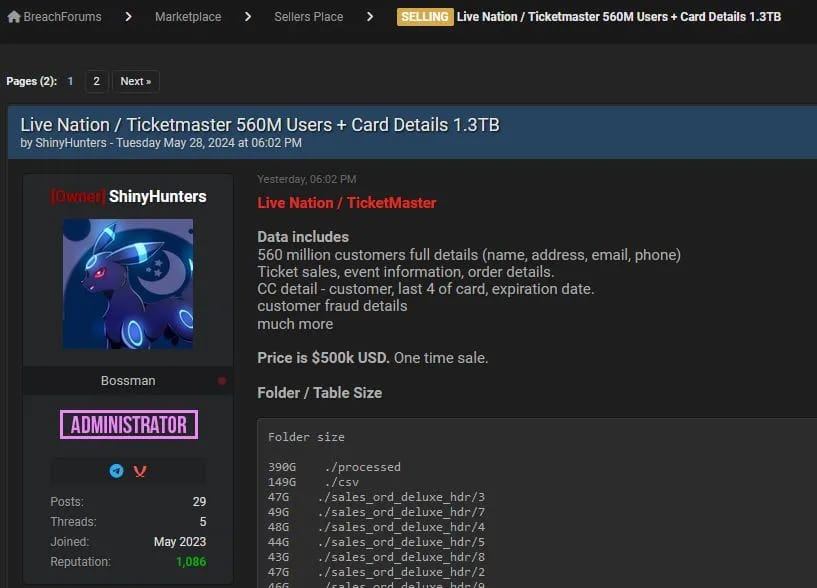
Source: Malwarebytes
ShinyHunters didn’t do this attack. Some unknown threat actors did. But ShinyHunters did them a solid by posting the info.
But wait, there’s more! Two days later, on May 30, 2024, ShinyHunters dropped another data dump. This time for Santander Bank. Based on the post, that data dump included information on the following:
30 million customers
6 million account numbers and balances
28 million credit card numbers
HR employee lists
Consumer citizenship information
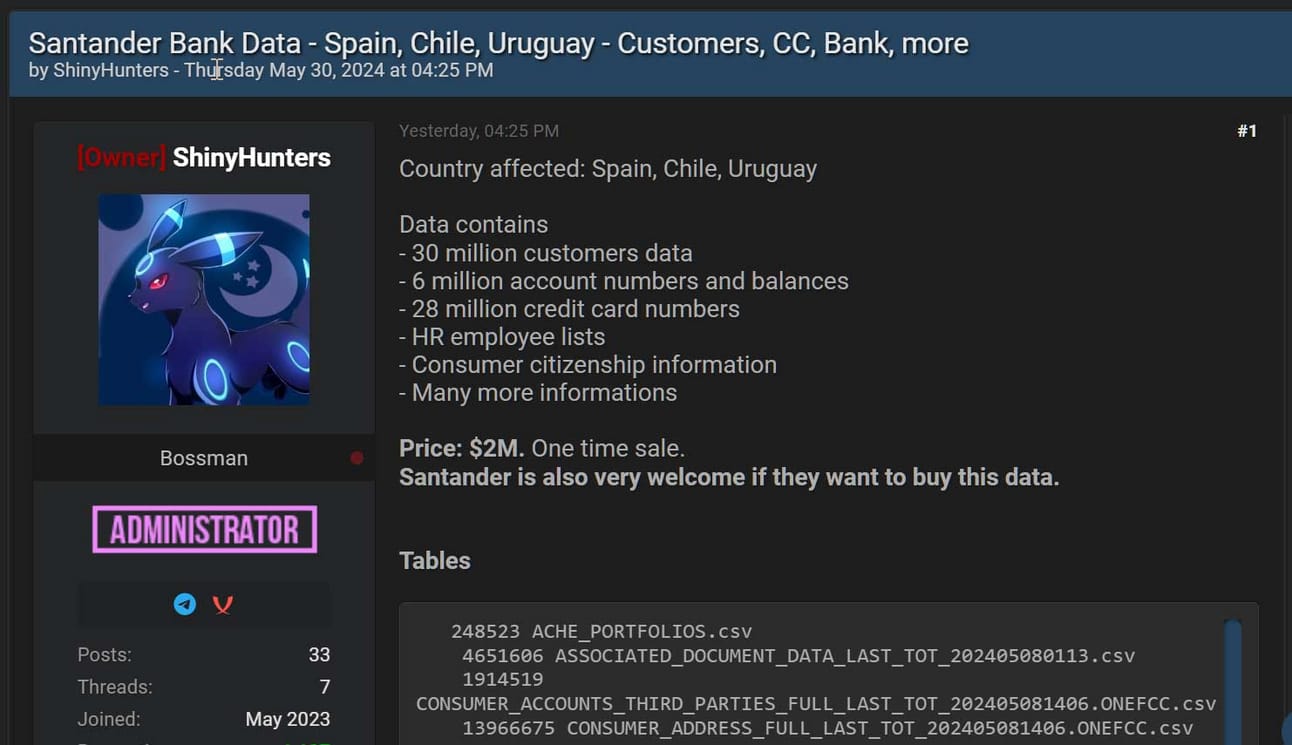
Source: Bleeping Computer
Okay, that’s two major data dumps…coincidence? Here’s where things get interesting. Livenation and Santander said the compromise occurred due to unauthorized access to a third-party database. Tell me more…both companies used the same third party, Snowflake. Uh oh…
Immediately, fingers pointed to a big issue at Snowflake, who quickly splashed cold water on the situation with an update to set the record straight on what was happening.
We believe this is the result of ongoing industry-wide, identity-based attacks with the intent to obtain customer data. Research indicates that these types of attacks are performed with our customers’ user credentials that were exposed through unrelated cyber threat activity. To date, we do not believe this activity is caused by any vulnerability, misconfiguration, or malicious activity within the Snowflake product.
Okay, so wtf is going on then? Oh, just the standard stolen credentials and no MFA. Yeah, that old thing we’ve been talking about for years. It appears as though the threat actor has been collecting Snowflake account credentials through infostealers. After finding accounts that had no MFA enabled, they used a tool not so eloquently named “rapeflake” to extract data, lots of data, from those accounts. There are reports that they are extorting the victims and dropping the data on BreachForums for those who don’t pay.
If you are a Snowflake customer, you can take the following steps to check if you’ve been compromised.
So yeah, this is your weekly reminder that the behind-the-scenes stories of so many major cyber attacks are about as exciting as those wonderful weekends you spend in your comfy clothes binge-watching Netflix. Great and enjoyable outcome, but not a lot of work that needs to go into it.
News
What Else is Happening?
🏧 Did you know that ATMs can get infected with malware? Yup. A threat actor is selling ATM malware, claiming it will work on 60% of ATMs worldwide, has a 99% success rate, and can net $30K per ATM. Yahtzee?
🎃 An unknown attacker bricked 600K home routers of customers at a single internet service provider (ISP). This happened in October 2023, and the only ones that noticed were the customers who complained on the ISP’s forums. Each customer had to have a new router sent to them to have internet again.
🚪 A 31-year-old Russian individual was indicted for his actions as an access broker. An access broker hacks into organizations (or buys access from those who did) and sells that access to other cybercriminals. It’s easy for ransomware actors to buy access into an environment and then focus on deploying ransomware.
☠ Threat actors are using fake anti-virus websites to trick users into downloading malware. These are often promoted through Google Ads so users click on the website for the malicious website. The websites look like the real vendor’s website, so unsuspecting users thinking they’re securing their systems are downloading spyware / infostealers to their systems.
🔍 Some attacker apparently thinks that people still play Minesweeper. Ukraine’s CSIRT team found a malicious email campaign targeting US and European financial institutions. The payload includes a Minesweeper clone and malicious code that downloads and installs SuperOps RMM, a remote access tool.
🛡 Law enforcement went full Avengers to disrupt Thanos's major botnets in Operation Endgame. Their opening move included arresting four suspects, taking down over 100 servers worldwide, and seizing over 2,000 domain names that supported the botnet infrastructure. One thing is certain: law enforcement is stepping up their game by trolling these attackers to show that hackers are not operating with immunity.
If you enjoyed this, forward it to a fellow cyber nerd.
If you’re that fellow cyber nerd, subscribe here.
See you next week!

