Have you noticed Google’s new AI Overview at the top of your searches? Well, we’re now learning that it can’t take a joke. But instead of storming off in a hissyfit, it just gives us bad…and I mean really bad…information.
Things like using “non-toxic glue” to keep the cheese from slipping off your pizza or leaning too hard into dad jokes saying the cause of a car blinker not making a sound was because of low-blinker fluid…classic.
Today in the cyber world, we’re covering:
Law enforcement makes a significant arrest.
Is the UK banning ransomware payments?
Don’t forget about supply chain attacks.
-Jason
Spotlight
Straight to Jail

Gif by nounish on Giphy
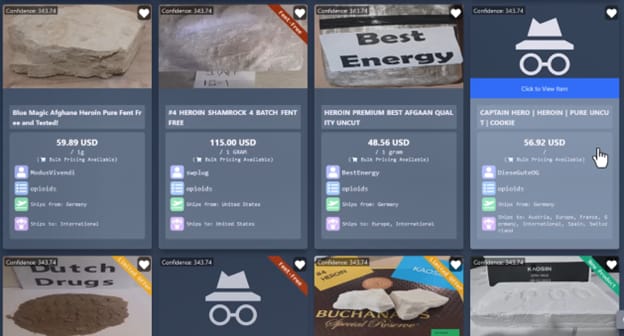
If you operate a dark web marketplace that facilitates the sale of over $100 million worth of illegal drugs, you’re going to make friends with the DEA. But not like “BFFs sharing ice cream” kind of friends. It’s more like that kind of friend you want to punch in the face every time they open their mouth because they’re so annoying…so I guess they are not a friend at all…
Good talk. Anyway, someone really bad went to jail. That someone was Rui-Siang Lin, a 23-year-old Taiwanese male. And because you’re not a true cyber mastermind without a cool hacker name, he went by “Pharoah,” which we will too. Not because it’s cool but because it’s easier to type.
In October 2020, Pharoah stood up the Incognito Marketplace on the dark web. Per the DOJ’s announcement, “Incognito Market sold illegal narcotics and misbranded prescription medication, including heroin, cocaine, LSD, MDMA, oxycodone, methamphetamines, ketamine, and alprazolam.” So, it's not your standard CVS pharmacy…
Here’s a screenshot that no one reading this should have seen because you’re all upstanding citizens who avoid the dark web.
The marketplace was operational until March 2024, when Pharoah pulled an exit scam. Perhaps he was feeling the heat from the feds and wanted to cash out?
Before his arrest, Pharoah worked in the technical corps at Taiwan’s embassy in St Lucia. Before his expected discharge in July, he applied for leave to travel to Singapore. One problem…that flight had a connection at JFK airport in NYC. And that’s where law enforcement scooped him up.
I was about to make a Scruff McGruff joke here about how crime doesn’t pay. But I just learned that the former actor who played him was sentenced to 16 years in prison after police found 1K marijuana plants, 27 weapons, which included a grenade launcher (naturally), and 9K rounds of ammunition in his home.
I guess all that crime he took a bite out of gave him severe indigestion.
Deep Dive
Drastic Measures to Stop Ransom Payments

Giphy
The UK is preparing to propose drastic measures to curtail the growing number of ransomware attacks. They floated some ideas, including:
Requiring all victims to report ransomware attacks to the government.
Requiring any victim who needs to pay a ransom to obtain a license before paying.
Exploring the ban of any ransom payments.
Of course, this has spurred the growing debate on whether ransom payments should be banned. Ransom payments are nothing new. Pirates once kidnapped Julias Ceaser looking for some quick booty…umm…that could be misconstrued…ahem…moving on. The idea of banning ransom payments is also not new.
In 1991, Italy banned families from making payments to organized crime groups, aka the Mafia, when their loved ones were kidnapped. Knowing that people would still be tempted to make the payments, the law froze families' assets to prevent them from paying ransom.
While initial figures seemed to show that it was working, the analysis was flawed. First, as the chart below shows, the number of kidnappings had already declined for years.
Second, victims stopped reporting the crime or found other people to pay the ransom on their behalf. I’m shocked…absolutely shocked at that notion.
Oh, and Columbia tried this as well. It was in response to increased kidnappings in the time that Pablo Escobar was building his drug empire. It lasted about 11 months until the courts reversed the decision, citing the restrictions violated the victim’s family's right to privacy. Womp womp.
The US isn’t quite there for banning ransomware payments in mass. Instead, they have prioritized disruption against ransomware actors' infrastructure, and a ransomware task force has provided an alternative path. This alternative path seeks a middle ground, recognizing that an outright ban on ransomware payments may cause more harm than good. This table from Matt Kapko at Cybersecurity Dive has the ransomware task force’s 16 proposals.
Milestones | Status |
|---|---|
Develop a national ransomware framework to standardize preparation and response. | Awaiting support |
Create a national campaign to raise awareness and understanding of ransomware. | Awaiting support |
Provide financial incentives to entities that comply with national ransomware framework. | Awaiting support |
Mandate limited baseline security measures for critical infrastructure organizations. | Underway |
Ensure robust information-sharing across cryptocurrency exchanges, incident responders, insurers, and law enforcement. | Done |
Issue formal statements targeting ransomware criminals through diplomatic channels. | Done |
Form an international law enforcement coalition to target ransomware criminals. | Done |
Establish working groups and joint ransomware task forces to coordinate disruption efforts. | Done |
Require cryptocurrency exchanges to comply with the law. | Underway |
Consistently engage in sustained disruptive actions against ransomware infrastructure. | Done |
Use victim data in cyber insurance market to support global law enforcement efforts. | Awaiting support |
Create a ransomware response fund to aid recovery and disincentivize ransom payments. | Awaiting support |
Communicate existing policies and prohibited activities to insurer consortiums. | Awaiting support |
Remove tax deductibility allowances for ransomware payments. | Awaiting support |
Mandate entitites report ransomware incidents to the federal government. | Underway |
Require organizations to conduct due diligence and cost-benefit analysis prior to paying ransoms. | Underway |
Any route we take to curb ransomware will involve pain. Some paths may have less pain, but we can’t escape hard decisions. While we debate the merits of each approach, there’s one thing that organizations should continue to do. Keep improving backups!
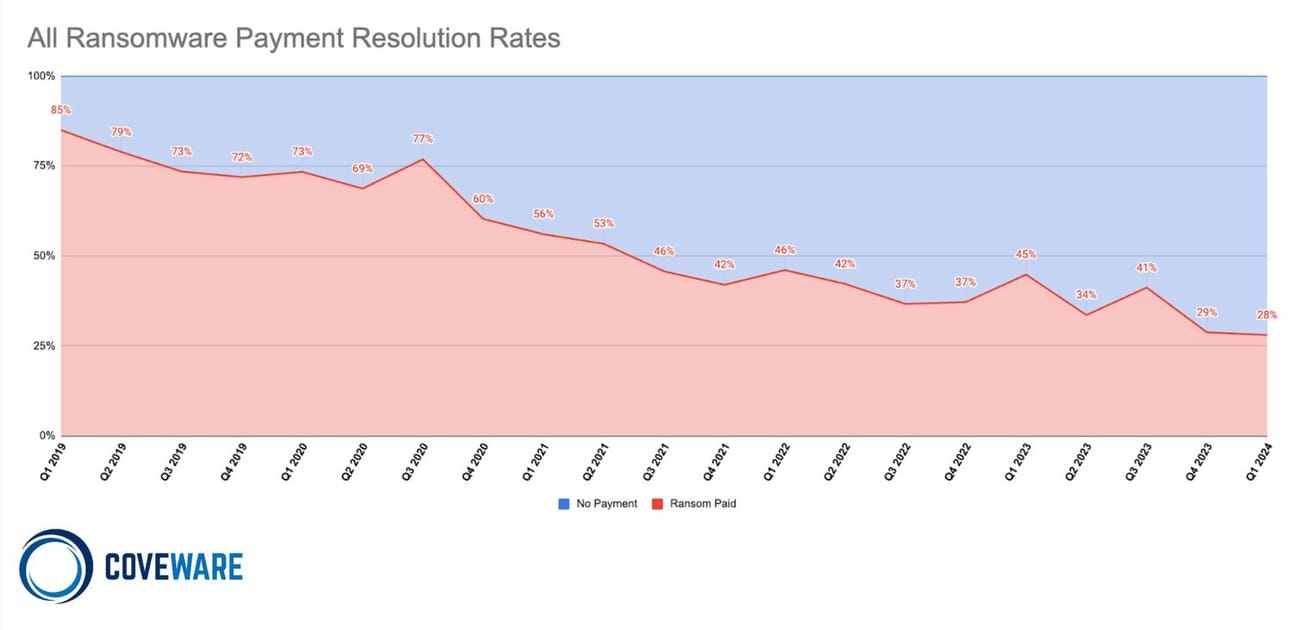
Coveware has seen that the percentage of victims paying a ransom continues to decrease. This could be attributed to many things, but one area is that organizations are getting better at doing backups and securing them! I see it as one of the major reasons why more ransomware groups are using data theft as a way to increase pressure to pay.
News
What Else is Happening?
🛒 Walmart’s cybersecurity research team (yes, low prices and a great security team) is still flexing 💪 after discovering a new malware loader last year dubbed LATRODECTUS (okay, good security team, bad at names…). Elastic security found that the loader is gaining steam in the cyber underground. Delivered through phishing emails, the loader sends system information to the attacker and then downloads malware to the system.
💰The SEC announced amended rules that “govern the treatment of consumers’ nonpublic personal information” for certain financial institutions. The changes include notifying the SEC within 30 days of any unauthorized access to customer information (or reasonably likely to have occurred) and requiring a written incident response plan. While it’s a step in the right direction, it also provides more feelings of security than actually securing the data in the first place.
🛡 Attackers are throwing steaks with sleeping pills over the fence to EDR tools to make their attacks easier. The GHOSTENGINE crypto miner (we need to stop with the stupid names) drops vulnerable software drivers onto the system, exploits them to terminate any running EDR processes, and then drops a crypto miner on the system.
👩⚖ The latest supply chain attack targeted software that provides audiovisual recording capabilities to more than 10,000 courtrooms around the world. The Justice AV Solutions (JAVS) software had malicious backdoor code as early as February 21, 2024. This would allow attackers to take full control of the systems.
🎉 While I don’t like to root for hackers, sometimes it’s warranted. A hacker defaced a spyware app’s website and dumped their source code and databases.
🔒 Not all ransomware needs to encrypt files. For lazy efficient attackers, they use Windows native BitLocker full-volume encryption to lock users out of their systems. A new ransomware variant, ShrinkLocker, stepped away from the RaaS groups and opted for BitLocker instead to encrypt systems and demand money for the key to unlock the devices.
🚗 It takes someone special to steal money from Medicaid programs or use romance scams to trick someone into sending you their life savings. A 31-year-old Georgia man is one of those special people. He’s getting 10 years in prison for laundering over $4.5M, which he used to buy expensive cars, like a Ferrari, and fancy jewelry.
🤦 I wrote last week about Google accidentally deleting a customer’s entire Cloud environment. Well, Google released details of why…it was all thanks to someone forgetting to enter information into a single field a year ago. Little did anyone know, but when the customer’s environment was stood up last year, it had a one-year shelf-life because of the blank parameter. They had been sitting on a time bomb.
If you enjoyed this, forward it to a fellow cyber nerd.
If you’re that fellow cyber nerd, subscribe here.
See you next week!