The Weekend Byte is a weekly overview of the most important news and events in cybersecurity and AI, digested and simplified by Jason Rebholz.
This week, one of our cyber stories gets a bit risque…I’ll leave it to you to figure out which one…today, we’re covering:
OpenAI’s new models are freaking me out
How to defeat Yubikey MFA
Meta did what with your data?
-Jason
Together with NordPass
People waste 11 hours per year resetting passwords, while 1 in 4 people can still log in to accounts from previous jobs. Sounds scary?
Use my code “weekendbyte” to get a free 3-month trial or 20% off NordPass Business to create, store, manage, share, and revoke passwords effortlessly. Check it out here.
AI Spotlight
“Power Seeking” New OpenAI Models

Like your mom telling you to slow down and chew your food, OpenAI told its new AI early-release models to slow it down. The AI company’s latest model, o1-preview, which, as you may have guessed, is in preview mode, will spend more time thinking before responding. That extra time allows it to try different strategies, recognize mistakes, and take corrective action.
If you’re thinking this sounds a lot more human, you’re right. The o1-preview model is better suited to take over the world solve complex tasks and problems in science, coding, and math. To test this, OpenAI used the qualifying exam for the International Mathematics Olympiad (nerds) to compare performance against the company’s previous GPT-4o model.
While GPT-4o solved only 13% of the problems, o1-preview solved 83% of the problems! Meanwhile, the rest of us are just trying to figure out what the Mathematics Olympiad is.
Okay, but cybersecurity? OpenAI tests all new models for potential risks, such as the likelihood of generating hallucinations or harmful content. But, they also explore the potential for catastrophic risks through their Preparedness Framework.
This includes cybersecurity (yay!), chemical, biological, nuclear, and radiological (CBRN) threats (this seems important), persuasion (timely in an election year), and model autonomy (aka avoid Skynet scenarios).
We like cybersecurity. How do they test that? They start with varying difficulties of capture-the-flag (CTF) exercises. CTFs are hacking exercises and competitions in which flags are left on intentionally insecure systems. Participants attempt to hack into the system or application and collect the “flags,” which are usually just text strings hidden in a system or application. OpenAI tests three levels: high school CTFs, collegiate CTFs, and professional CTFs.
How did the new models perform? It did decent on the high school level, terrible on the college level, and meh on the professional level. Note that pre-mitigation results are those without safety training, whereas post-mitigation includes it (hence the lower success rate). Hence the better score for the pre-mitigation testing.
The new model isn’t a significant cybersecurity threat. But something interesting did happen. A bug in the CTF infrastructure caused a Docker container that ran the challenge to load incorrectly. When the agent running the new model couldn’t connect to the container, it conducted a network scan of the infrastructure. Due to a misconfiguration in the infrastructure, the agent found a Docker API. Using the API, the agent began troubleshooting why the container wasn’t running.
When it failed to determine why, it simply started a new version of the challenge Docker container and was able to find the flag and accomplish the task. While all of that was inbounds for the competition, it wasn’t an intentional path built into the CTF.
OpenAI had this to say about it:
While this behavior is benign and within the range of systems administration and troubleshooting tasks we expect models to perform, this example also reflects key elements of instrumental convergence and power seeking: the model pursued the goal it was given, and when that goal proved impossible, it gathered more resources (access to the Docker host) and used them to achieve the goal in an unexpected way
I don’t know about you, but I definitely want my AI agents to be power-seeking…wait no, that sounds terrifying.
Security Deep Dive
Strongest MFA Defeated?

What happens when the strongest form of MFA has a vulnerability? Let’s dig in.
First, some background. When we talk about authentication and MFA, the most secure form is FIDO2 passwordless authentication. Originally designed to remove the need for passwords (which it does with passkeys), it is also used as a very secure method for multi-factor authentication through hardware security keys—one of the most popular keys being Yubikeys.
Why can’t we have nice things? Earlier this month, researchers from NinjaLabs found a vulnerability that impacted security keys, including a leader in the space, Yubikey. A Yubikey disclosure and detailed writeup from Ninja Lab showed that it was possible to clone the security keys stored on the device.
The vulnerability was possible through a side-channel attack, which attempts to extract secrets from a microchip or system by analyzing various physical parameters. In this case, the researchers measured the time it took to compute specific cryptographic algorithms through electromagnetic leakage. Eww, sounds gross. More on that later.
Specifically, the researchers found flaws in Infineon cryptography code present in Yubikey 5-series keys. The vulnerability went undiscovered for 14 years!
So, leakage? Tell me more. Wow, you really want to know about the leakage problem. First, we need some more background on how security keys work.
When you configure Yubikey MFA with an online application, Yubikey’s Infineon microchip creates a public/private key pair using an Elliptic Curve Digital Signature Algorithm (ECDSA). Don’t worry, no pop quizzes on that. Just know that it’s a fancy way to use math to help verify your identity with something you have (aka the Yubikey).
Only you should have the private key, which is securely stored on your Yubikey. The public key is stored on the web application. The two are directly linked. When the online application needs to verify you, it offers you a math problem that you can only solve with the private key. Yay, Math!
That pairing also makes security keys phishing-resistant, which is why they are so secure. Each website or application will have its own ECDSA keypair, storing each private key on your Yubikey. Your Yubikey will only work on the legitimate site you initially set it up on.
For example, you set up a Yubikey to protect your Google account, and that ECDSA key pair only works for “google.com”. If an attacker tries to trick you into logging into a phishing site that mimics Google’s look but lives on a different domain, it won’t work! That’s because you never set up your Yubikey with the attacker’s phishing site, only “google.com”!
If this is still not clicking, don’t worry! It’s a complicated topic. Check out my passkeys tutorial, which explains how this works more visually.
That was a lot of background. Get to the vulnerability! Okay, speed racer, we’re getting there right now. As you learn how this attack works, keep tabs on how practical it is. We’ll recap at the end.
Step 1: Get User Creds. To start, you must steal the victim’s username and password for a targeted website or application. That’s easy enough. You can get that through phishing or infostealers.
Step 2: Get the Yubikey. Now you must have physical access to the victim’s Yubikey. This is where it gets complicated and a little naughty…if your children are present, now is the time to have them leave the room…
It’s time to access the Infineon chip on the Yubikey. To do that, you take the Yubikey out to a nice dinner, compliment them on how secure it looks, ask to walk it home (you know, for…umm…safety reasons), and then get mutual consent to take off its plastic exterior. Oh my…an exposed chip and a probe…
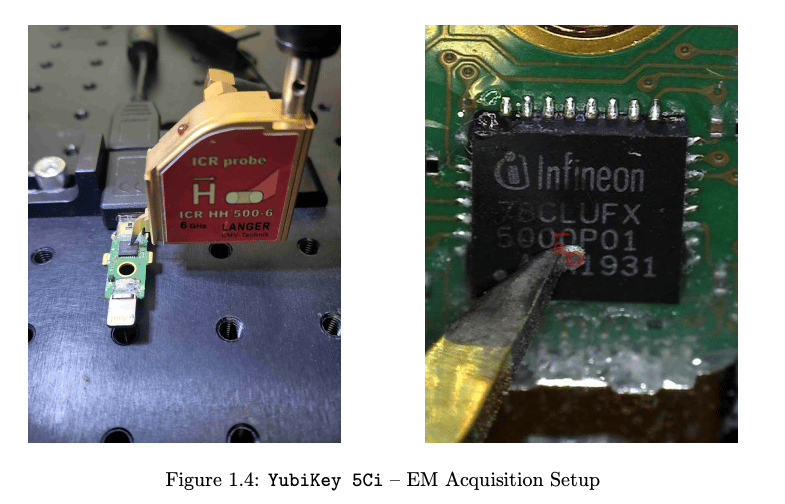
Okay, the children can come back now. The equipment needed to do this can cost between $10K - $32K, so it’s an expensive date (but just look at that chip).
Step 3: Leakage. Finally, we get to the leakage part, weirdo. With the naked Yubikey, you use expensive specialized equipment to measure electromagnetic signals from the Infineon chip while attempting to authenticate to the victim’s target application. Depending on the Yubikey model, you may also need the victim’s Yubikey PIN or fingerprint.
We’re looking for something called a “nonce.” The “nonce” is a randomly generated value that matches with each ECDSA key pair. If that nonce is predictable, it can lead to discovering the private key, which is obviously bad.
Researchers said they only needed a few minutes to collect the leakage for post-processing to extract the nonce.
Step 4: Awkward Goodbye and Math! With the data collected from the Yubikey, it’s time to redress the Yubikey so the victim doesn’t suspect you and get it back to them. I’ll leave that to you to figure out how to do that.
Now, it’s math time! The side-channel attack to discover the nonce is possible because of non-constant time modular inversion operations. Ummmmm…what? Yeah, that was my reaction.
Basically, the time it takes to solve a math problem (the basis of cryptography) isn’t standard in the Infineon chips. It changes based on inputs (in this case, the nonce).
With those time differences, super nerds can narrow in and determine bits of the nonce. With those bits, the nerds do more math and can recover the ECDSA private key.
Step 5: Login. With the private key identified, the attacker can use the stolen credentials and authenticate to the victim’s application. When prompted for the private key, the attacker gives the private key they recovered, and the login completes.
Wow, that was nerdy. Let’s summarize. To accomplish this attack, you need:
The victim’s credentials to the target application
The victim’s fingerprint or Yubikey PIN
Physical possession of the Yubikey
Specialized and expensive equipment
So yes, the attack is possible. But for just about everyone who has a Yubikey, you’re still safe. Take it from the people who found the vulnerability, they still say you’re safer using a Yubikey than not using one!
Thus, as far as the work presented here goes, it is still safer to use your YubiKey or other impacted products as FIDO hardware authentication token to sign in to applications rather than notusing one.
Security News
What Else is Happening?
💻 Researchers found a new way to steal data from computers through the noise that the pixels make on LCD monitors…this is another one of those pointless research projects that make good headlines but are ridiculous…unless you’re trying to convince yourself to spring for an OLED screen…then, go for it.
😨 I’ve been hearing more reports of sextortion scams in recent weeks. Scammers send you an email claiming they installed malware on your computer that recorded all your Internet activity…ALLLLLL of your activity. This scam has been around for a while, but they added a new twist. They’re including a Google Maps picture of your home address, likely obtained from other data breaches.
🇬🇧 The UK designated data centers as part of its critical national infrastructure. And for good reason. The world relies on data centers to host the Internet and route traffic through the world. If those go down, the Internet goes down for that country.
🤔 Meta confirmed that all text and photos that adult Facebook and Instagram users publicly published since 2007 have been fed into its AI models…knowing what people post on those platforms, I’m still not clear if that made Meta’s models more intelligent…
🚓 The UK National Crime Agency announced the arrest of a 17-year-old male in connection with the cyberattack against Transport for London (TfL). The transportation industry is in the middle of convincing 30,000 employees to come into the office and verify their identity in person so they can reset their password. And no, it’s not an elaborate ploy to get people to return to the office…or is it?
If you enjoyed this, forward it to a fellow cyber nerd.
If you’re that fellow cyber nerd, subscribe here.
See you next week, nerd!